
On September 10, 2025, CISA published its “CISA Strategic Focus: CVE Quality for a Cyber Secure Future” vision document, announcing that the cybersecurity industry is entering what CISA calls the “Quality Era” of the CVE Program: a deliberate shift away from the raw expansion of vulnerability coverage and toward enhancing the accuracy, reliability, and accessibility of CVE data.
This article is the first in a series of 4 articles which will also discuss how CISA’s changes will affect how vulnerability exposure data is consumed in this era of increasing AI assistance and automation in cybersecurity, how enterprises can better align with CISA’s vision for transparent vulnerability disclosure, and ultimately the regulator’s new role in the cyber supply chain itself.
The growth era
In the earlier “Growth Era,” the emphasis was on cataloging as many vulnerabilities as possible, increasing the number of CVE Numbering Authorities (CNAs) and accelerating publication timelines. But this growth came at a cost: inconsistent metadata, patchy CVSS scores, and variable CWE classification often left security teams with too little context to prioritize effectively. As a result, operational backlogs ballooned while exposure remained unresolved.
This change comes at a critical moment. Security teams and IT operations are drowning in alerts, many of which lack sufficient detail to differentiate real threats from noise. Incomplete or ambiguous CVE records force teams to supplement data manually or take conservative, time-consuming routes to risk reduction. For MSPs and IT leaders managing distributed infrastructure, these inefficiencies scale quickly and contribute to unacceptable delays in remediation.

What’s new in data quality
The Quality Era reframes what defenders can expect from vulnerability intelligence. Instead of serving merely as identifiers, CVEs are evolving into rich, structured assets capable of supporting evidence-based remediation. The future isn’t just about knowing a vulnerability exists; it’s about understanding its real-world exploitability, business relevance, and resolution path from the moment it’s published. Automation and machine learning are also playing a critical role in this transformation. CISA-backed initiatives like Vulnrichment and the Aggregated Data Pipeline (ADP) are leveraging verified metadata sources and natural language processing to enrich CVE records automatically. This reduces ambiguity around exploitability, impact, and remediation, while offering a consistent structure that security tools can ingest directly. The more consistent and complete the underlying data, the more reliable the downstream outputs for scoring engines, dashboards, and patching tools.
One of the most promising indicators of progress in the Quality Era is the sharp rise in enriched CVE entries. According to a recent CISA factsheet, nearly 80% of CVEs published by CNAs now include CVSS (Common Vulnerability Scoring System) and CWE (Common Weakness Enumeration) metadata, representing more than 9% year-over-year improvement. This improvement allows for better standardization in how vulnerabilities are scored and contextualized, removing much of the guesswork from triage and prioritization workflows.
To illustrate this transformation, consider the following comparison:
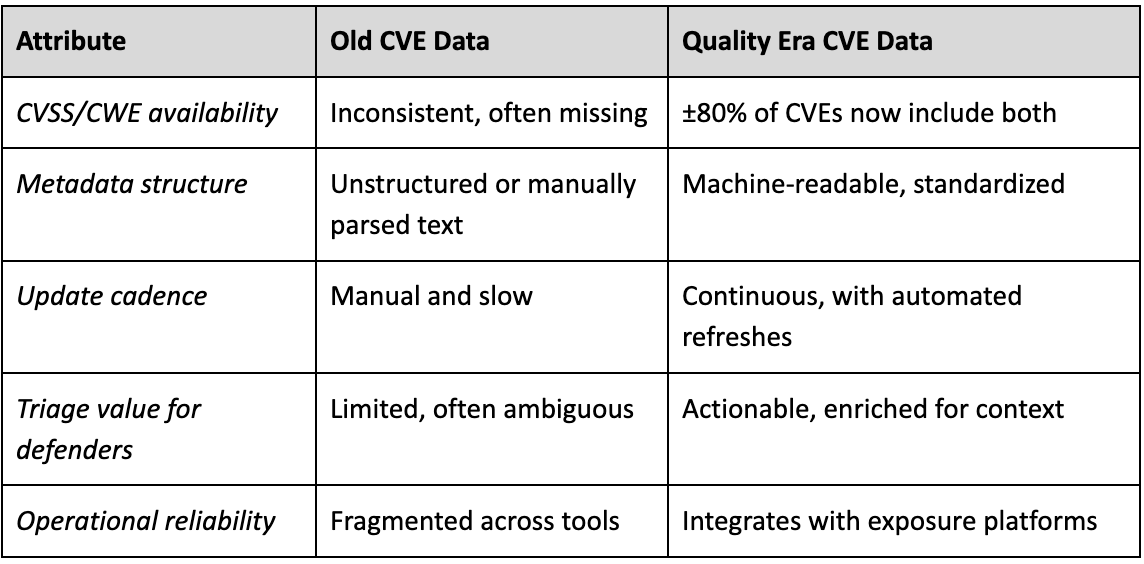
This shift turns CVE data from a compliance checkbox into an operational resource for real-time risk management.

Operational impact for security and IT teams
The practical value of the Quality Era lies in how enriched CVE records reshape day-to-day security operations. By embedding consistent CVSS scores, CWE tags, and structured metadata into vulnerability entries, the CVE Program is turning a formerly noisy signal into a reliable operational asset. Instead of vague entries that leave defenders guessing, enriched CVEs now provide the information required to assess risk at a glance and act decisively.
This has direct, measurable impact across key security workflows:
- Sharper triage decisions: Enabling faster, more confident triage through enriched records, reducing ambiguity around severity, exploitability, and system relevance.
- Less scanner duplication: Normalized metadata reduces false positives and overlapping alerts from disparate tools, easing alert fatigue and ticket sprawl.
- Shorter remediation cycles: Better context up front reduces friction between security, IT, and dev teams, which can accelerate coordination and approvals in change control workflows.
- More actionable SLAs: Accurate CVE data helps teams track SLA-bound fixes more precisely and communicate remediation timelines with greater confidence.
- Stronger executive reporting: Clean, structured data feeds directly into dashboards and board-ready metrics, improving transparency, risk communication, and post-event debriefs.
In practice, this means teams spend less time validating vulnerability records and more time resolving them. Security, IT, and development can collaborate more effectively when everyone has access to consistent information. From patch planning to root cause analysis, the operational gains compound across every part of the remediation pipeline.

How to prepare now
The CVE Quality Era brings richer data, but realizing its benefits requires targeted operational updates. Security and IT teams should begin aligning their tooling, triage logic, and metrics to handle enriched vulnerability intelligence effectively.
Update ingestion and tool compatibility
Firstly, ensure that your scanners, CMDBs, and ticketing systems can ingest and display structured CVE fields like full CVSS vectors, CWE tags, and exploit status. Some platforms may require schema updates or enrichment plugins to expose this data at the point of triage. Regularly verify that enriched CVE data is visible and actionable in your dashboards, ensuring analysts can interpret CVSS, CWE, and exploit details without manual lookup.
Normalize CVE metadata across workflows
Incomplete or inconsistent metadata slows response. Build routines to normalize CVSS and CWE fields where missing, or flag low-fidelity records for review. Prioritization models should assume this data is present and required. Automate enrichment where possible so triage teams always see complete, standardized data, avoiding inconsistencies or missing context that could slow prioritization.
Evolve policies toward contextual risk
Shift from CVSS-only approaches to risk-based models that factor in exploitability and asset criticality. Integrate CISA’s Known Exploited Vulnerabilities (KEV) catalog into daily workflows, and treat KEV-listed CVEs as urgent regardless of base score. Automate enrichment where possible so triage teams always see complete, standardized data, avoiding inconsistencies that slow prioritization.
Set early metrics for triage and resolution
Measurable gains help validate the transition. Use these metrics to track progress over time, refining workflows as Quality Era data becomes the new baseline. Focus on short-term KPIs such as:
- Metadata completeness: Percent of CVEs with CVSS and CWE data at triage.
- Time-to-triage (MTTT): Mean time from alert to triage decision.
- KEV resolution time: Average days to close known-exploited CVEs.
Aligning now ensures that your vulnerability management program can turn Quality Era inputs into faster, smarter, and more defensible remediation outcomes.
Your vulnerability data just leveled up. Did you?
The Quality Era of the CVE Program marks a deliberate pivot from sheer volume to strategic clarity. By emphasizing data accuracy, consistent enrichment, and accessibility, it enables security teams to make faster, more informed decisions. The result is not just more CVEs, but CVEs that matter; records that improve triage, shorten response cycles, and align remediation efforts with real-world risk.
Part 2 of this series on the CISA Quality Era, “AI, Automation, and APIs: How CISA’s Roadmap Will Transform Vulnerability Intelligence Consumption”, will explore how these improvements in data quality unlock deeper levels of automation and enable practical exposure management workflows that close the loop from detection to remediation. From ML-driven enrichment to prioritized patch orchestration, the next phase is about turning enriched data into coordinated action. For teams looking to operationalize this shift now, vRx by Vicarius offers a purpose-built platform that already supports the Quality Era’s enriched data model.
Book a demo now to see how smarter CVE intelligence can power continuous risk scoring, automated patching, and measurable exposure reduction. Let us help to bring the future of vulnerability management within reach today.












