
Comprehensive Cybersecurity Glossary
100 Vulnerability & Patch Management Terms
Active Directory
Microsoft’s centralized directory service for managing user accounts, devices, and access in enterprise networks. In a security context, maintaining up-to-date patches and strict controls on Active Directory is critical to prevent attackers from exploiting known vulnerabilities in this ubiquitous identity management system.
Agent-based
A security or scanning approach that relies on lightweight software agents installed on endpoints to collect data or enforce policies. Agent-based vulnerability scanning can provide deep insight into systems (including offline or remote devices), enabling more thorough vulnerability management and patch deployment. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Agentless
A method of scanning or managing devices without installing local software agents. Agentless vulnerability scanning uses network protocols and credentials to assess systems for missing patches or misconfigurations, simplifying deployment but potentially with reduced visibility compared to agent-based solutions.
Asset Inventory
A comprehensive list of all hardware and software assets in an organization’s IT environment. An accurate asset inventory (including servers, workstations, applications, and IoT devices) is foundational for vulnerability management, as it enables security teams to discover assets, track their patch status, and ensure no device is left unmanaged. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Asset Management
The process of tracking and maintaining IT assets throughout their lifecycle to support security and operations. In vulnerability management, asset management involves grouping assets (by type, location, etc.), monitoring their software versions, and prioritizing patching efforts to protect critical assets and ensure compliance with security policies. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Attack Surface
The sum of all points where an unauthorized user could try to enter or extract data from a system. A smaller attack surface (achieved through system hardening, network segmentation, and removing unused services) means fewer vulnerabilities exposed to attackers, making it easier for security teams to defend and manage vulnerabilities.
Authentication
The security process of verifying a user’s identity before granting access to systems or data. Strong authentication (e.g. using multi-factor authentication) is an IT best practice that reduces the risk of unauthorized access, ensuring that even if vulnerabilities exist, only legitimate users (with proper credentials) can log into enterprise resources.
Authorization
The process of granting or denying specific access rights or permissions to an authenticated user or system. Effective authorization (often implemented via role-based access control) ensures users can only perform actions or access data necessary for their job, limiting potential damage if an account is compromised or a vulnerability is exploited.
Automated Remediation
What is Automated Remediation - Automated Remediation refers to a platform’s ability to detect, analyze, and fix security exposures such as vulnerabilities and misconfigurations across hybrid IT environments by applying patches, scripts, or patchless protections without manual intervention.
Why Automated Remediation Matters - Today’s environments generate thousands of alerts daily many due to unpatched software, misconfigurations, or isolated tools. Manual remediation can’t keep pace and often introduces operational risk. Vicarius vRx addresses this by automatically correlating exposure to root causes, validating compensating controls, and executing safe, business-aligned remediations eliminating noise, speeding up response, and fortifying defenses with minimal human effort .
Key Capabilities & Benefits: Automated Remediation in Action
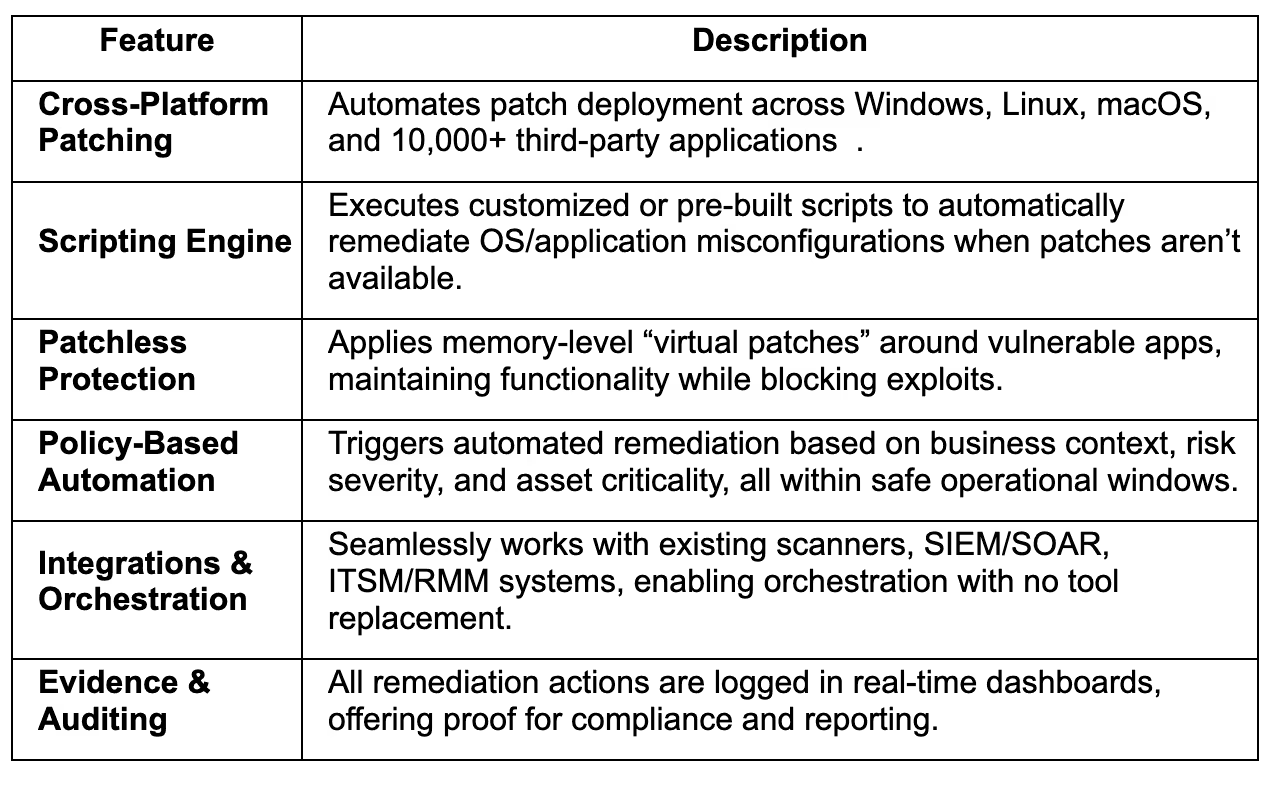
How It Works
- Discover & Prioritize: Ingests scan and telemetry data to find exposures across cloud, endpoint, network, and third-party systems.
- Contextualize: Assesses real-world exploitability using intelligence on asset importance, environment context, and active threats .
- Remediation Options: Offers multiple fixes, patches, scripts, or virtual shields to match operational and business constraints .
- Automate & Execute: Uses policy-based workflows to automatically roll out the safest, most effective remedy, restart services, update OS, reconfigure systems, or enable exploit prevention.
- Audit & Report: Continually logs actions and outcomes in dashboards for visibility, compliance, and governance.
Proven Impact: Automated Remediation at scale
- Recognized by Gartner in June 2025 in preemptive exposure management and automated remediation, effectively managing exposures across OSs and over 10,000 apps.
- MSP integrations (e.g., Atera) achieved 80% faster patching, translating to reduced downtime and more efficient remediation workflows.
- Case studies demonstrate rapid, safe fix deployment even enabling script-based remediations in absence of vendor patches.
Real-World Use Cases
- Agent/Agentless OS-Level Fixes: Harden endpoints automatically.
- One-Click Vulnerability Remediation: Immediate patching or shielding through user-approved workflows.
- Control Hardening: Proactively enforce configurations to reduce exposure surfaces.
- Threat Intelligence Enforcement: Apply new evidence and actions across environments automatically when new threat data is ingested.
Beyond Traditional Patching: Full-Cycle Automated Remediation
Vicarius advances beyond patch management by:
- Mapping exposures to their root causes, whether a missing patch, misconfiguration, or absent control.
- Selecting the safest remediation strategy based on context (e.g., avoid downtime by virtual patching).
- Validating business safety before deployment, ensuring no disruption to critical workflows.
Automated remediation with Vicarius vRx means closing the loop, from identifying exposures to deploying safe, context-aware fixes at scale without manual intervention. It ensures:
- Faster risk reduction
- Greater operational consistency
- Proven auditability
- Lowered burden on IT teams
In essence, Vicarius brings remediation to the forefront of security operations transforming vulnerability management from reactive to proactive, safe, and fully automated.
Automation
The use of scripts and tools to perform routine IT and security tasks without human intervention. Automation in patch management and vulnerability remediation allows organizations to rapidly deploy updates, configure systems, and remediate threats at scale, reducing human error and significantly speeding up the response to critical vulnerabilities. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
BYOD (Bring Your Own Device)
An IT policy allowing employees to use personal devices (laptops, smartphones, tablets) for work purposes. BYOD introduces security challenges, as personal devices may not be under full corporate control; organizations must enforce best practices (like mobile device management, mandatory updates, and access control) to manage vulnerabilities and ensure that personal devices accessing corporate data are secure and compliant.
Baseline Configuration
A documented set of secure settings and approved software versions for systems and devices. Maintaining a security baseline (e.g. default configurations aligned with CIS benchmarks or other standards) helps IT teams quickly identify when a system drifts from its hardened state, making it easier to spot vulnerabilities or unauthorized changes and ensure compliance with best practices.
Buffer Overflow
A common software vulnerability where a program writes more data to a buffer (memory space) than it can hold, overwriting adjacent memory. Buffer overflow flaws can be exploited by attackers to execute arbitrary code or crash systems, so identifying and patching these vulnerabilities is a top priority in vulnerability management to prevent exploits and maintain application security.
Bug Bounty
A program in which organizations offer rewards to ethical hackers for finding and responsibly disclosing security vulnerabilities in their software or infrastructure. Bug bounty programs supplement internal vulnerability management by leveraging the wider security research community to discover hidden flaws, ultimately leading to timely patches and improved security for the company.
CVE (Common Vulnerabilities and Exposures)
A publicly disclosed cybersecurity vulnerability assigned a unique identifier. The CVE system (maintained by MITRE) catalogs vulnerabilities in software and firmware, enabling organizations to track specific flaws (like “CVE-2025-12345”), assess their exposure, and prioritize patching. Security teams reference CVEs to ensure they address all known critical issues affecting their systems. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
CVSS (Common Vulnerability Scoring System)
An industry-standard method for rating the severity of security vulnerabilities on a numeric scale (0.0 to 10.0). CVSS scores (e.g. 7.8 High, 9.8 Critical) are used in vulnerability management to prioritize remediation efforts higher scores indicate more severe or easily exploitable vulnerabilities, helping IT and security teams focus on fixing the most dangerous issues first. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
CWE (Common Weakness Enumeration)
A categorized list of common software weakness types (such as buffer overflow, SQL injection, etc.) maintained as a community resource. Each CWE identifies a type of coding or design flaw that can lead to vulnerabilities. Developers and security analysts use CWE identifiers to understand the root cause of vulnerabilities, improving secure coding practices and informing better vulnerability remediation strategies (e.g. addressing the underlying weakness, not just the immediate bug).
Change Management
A formal IT process for reviewing and approving changes (like software updates, patches, or configuration changes) before implementation. Effective change management ensures patches are deployed in a controlled manner (often during maintenance windows), minimizing disruptions and verifying that security updates do not inadvertently impact system stability or violate compliance requirements.
Compliance
Adherence to industry regulations, security standards, and organizational policies designed to protect data and systems. In vulnerability and patch management, compliance often means meeting requirements (e.g. PCI DSS or HIPAA rules) by regularly scanning for vulnerabilities, applying critical patches within defined timeframes, and maintaining audit logs to prove that security controls are in place and effective. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Configuration Management
The practice of maintaining consistency of a system or product’s configuration (settings, installed software, and updates) throughout its life. Robust configuration management in IT security involves regularly auditing system settings, ensuring secure configurations (no weak defaults or open ports), and quickly correcting misconfigurations – all of which reduce vulnerabilities and help maintain a strong security posture.
Container Security
The protection of containerized applications and their underlying infrastructure (such as Docker or Kubernetes environments) from vulnerabilities and threats. Container security includes scanning container images for known CVEs, applying updates to base images, implementing runtime security controls, and managing container orchestrator settings to ensure that cloud-native applications remain compliant and secure against exploits.
Continuous Monitoring
An ongoing process of real-time or frequent security monitoring to detect new vulnerabilities, threats, or configuration changes as they arise. Continuous monitoring in vulnerability management involves using automated scanners and agents to regularly assess systems, promptly identify missing patches or new risks, and provide security teams with up-to-date information to remediate issues before attackers can exploit them.
Default Credentials
Pre-set login usernames and passwords that come with hardware or software (e.g. “admin/admin” for a new router). Default credentials are well-known to attackers, and if not changed, they represent a serious security vulnerability attackers can easily gain unauthorized access. IT best practices require replacing default credentials with strong, unique passwords to reduce the risk of compromise.
Denial of Service (DoS)
An attack that aims to make a system, service, or network unavailable by overwhelming it with traffic or exploiting a flaw to crash it. Some unpatched vulnerabilities can lead to DoS conditions (for example, a malformed request triggering a system crash). Robust patch management and network protections (like firewalls or rate limiting) are key defenses against DoS by ensuring stability and closing known loopholes that attackers might abuse.
Dependency Management
The practice of tracking and updating external libraries or modules that an application relies on. In cybersecurity, dependency management is crucial because vulnerabilities in third-party components (open-source libraries, frameworks, etc.) can put the entire application at risk. Automated tools (like software composition analysis) help identify outdated or vulnerable dependencies so organizations can promptly apply updates or patches to maintain a secure software supply chain.
DevSecOps
A cultural and technical approach that integrates security into DevOps workflows (“Development, Security, Operations”). DevSecOps emphasizes automating security checks (such as code scanning, container scanning, and configuration audits) throughout the software development and deployment pipeline. This ensures that vulnerabilities are identified and remediated earlier (shift-left security), and that applications and infrastructure are deployed in a secure, compliant state without slowing down agile delivery.
End-of-Life (EOL) Software
Hardware or software that is no longer supported by the vendor with updates or patches. End-of-life software becomes increasingly dangerous in an enterprise environment because new vulnerabilities will remain unpatched. Security teams should plan to upgrade or replace EOL systems, or isolate them if they must remain in use, to mitigate the heightened risk of unpatched security flaws being exploited.
Endpoint Management
The administration of end-user devices (desktops, laptops, mobile devices, servers) to ensure they are secure, updated, and in compliance with corporate policies. Strong endpoint management involves deploying patches, managing configurations (like antivirus and firewalls), and using MDM/EDR solutions so that each device is protected against known vulnerabilities and can be monitored for signs of compromise.
Exploit
A piece of code or technique that takes advantage of a vulnerability to execute unauthorized actions on a system. Exploits can range from simple scripts to sophisticated malware and are often used by attackers to gain control, elevate privileges, or cause damage. Once a vulnerability has a known exploit publicly available, it’s critical for organizations to expedite patching or implement mitigations, as the risk of attack is significantly higher. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
False Negative
In security scanning, a scenario where a vulnerability or threat exists but is not detected by the tool. False negatives are dangerous because they give a false sense of security; a critical vulnerability could go unpatched if the system fails to flag it. Using multiple scanning methods (credentialed scans, different tools, manual reviews) and keeping scanners updated can help minimize false negatives in vulnerability assessments.
False Positive
An incorrect alert indicating a vulnerability or threat that is not actually present. False positives in vulnerability scanning can overwhelm security teams with noise, leading to wasted effort or important issues being overlooked. Tuning scanning tools, using agent-based methods for accuracy, and cross-verifying findings help reduce false positives so teams can focus on genuine vulnerabilities that require remediation.
Firewall
A network security device or software that monitors and filters incoming and outgoing network traffic based on an organization’s configured security rules. Firewalls (including next-generation firewalls) act as a first line of defense by blocking unauthorized access and known malicious traffic, thereby protecting vulnerable services from external attacks. While a firewall doesn’t replace patching, it can mitigate certain network-based exploits by restricting access to vulnerable ports or applications.
Firmware Update
A patch or upgrade for the low-level software (firmware) that runs on hardware devices like BIOS, network routers, IoT gadgets, or printers. Firmware updates often include important security fixes for stability and vulnerability patches. An effective patch management program encompasses firmware alongside operating system and application updates, ensuring that attackers cannot target outdated firmware as a backdoor into otherwise secured systems.
GDPR
The General Data Protection Regulation, a European Union law focused on data protection and privacy. GDPR mandates organizations to protect personal data, which includes keeping systems secure from breaches. Under GDPR, companies must take appropriate cybersecurity measures (like timely patching of vulnerabilities that could lead to data leaks) and can face heavy fines if negligent security practices result in exposure of EU citizens’ personal data.
GRC (Governance, Risk & Compliance)
An integrated approach to align IT activities with business goals (governance), manage and mitigate risks, and meet regulatory requirements (compliance). In practice, GRC in cybersecurity involves setting security policies, performing risk assessments (including evaluating vulnerabilities), and ensuring compliance with standards. A strong GRC program will prioritize vulnerability management and patching as key controls to reduce organizational risk and satisfy audit requirements. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Gap Analysis
A process of comparing an organization’s current security posture or controls against desired standards or requirements to identify “gaps.” In vulnerability management, a gap analysis might reveal shortcomings such as missing patch management processes, incomplete asset inventories, or non-compliance with frameworks like ISO 27001. By highlighting these gaps, security teams and compliance officers can develop a remediation plan to improve defenses and meet all regulatory or policy requirements.
HIPAA
The Health Insurance Portability and Accountability Act, a US regulation that among other things requires healthcare organizations to secure protected health information (PHI). Under HIPAA’s Security Rule, healthcare entities must maintain proper security measures, including regular vulnerability scans, prompt installation of security patches, and documentation of remediation, to safeguard patient data and avoid breaches that could result from unpatched systems.
Hardening
The process of securing a system by reducing its vulnerability surface area, typically by disabling unnecessary services, removing default accounts, and applying secure configuration settings. System hardening complements patch management: while patches fix known software flaws, hardening secures the environment (firewall rules, registry settings, etc.) to protect against exploitation of both known and unknown vulnerabilities, thereby improving the overall resilience of the system.
Hotfix
A targeted update released by a vendor to quickly fix a specific critical issue, often a security vulnerability, outside of the normal patch release schedule. Hotfixes are typically developed and distributed in response to emerging threats (like an exploit in the wild) and can be applied to address the urgent problem. Organizations should test hotfixes when possible and apply them promptly, as they address high-risk vulnerabilities that can’t wait for the next Patch Tuesday or regular update cycle.
ISMS (Information Security Management System)
A framework of policies, procedures, and controls that systematically manages an organization’s sensitive data and cybersecurity processes. Often associated with standards like ISO 27001, an ISMS covers everything from risk assessment and security governance to incident response. Vulnerability management and patch management are critical components of an ISMS, ensuring that identified risks (e.g. software vulnerabilities) are promptly addressed as part of maintaining the organization’s security posture.
ISO 27001
An international standard that outlines best practices for establishing, implementing, and maintaining an Information Security Management System. Achieving ISO 27001 compliance means an organization has a comprehensive security program in place, including regular risk assessments, access controls, and vulnerability management. As part of ISO 27001’s requirements, companies must have processes to identify and patch vulnerabilities in a timely manner to protect the confidentiality, integrity, and availability of information.
Incident Response
A structured process that organizations follow when a security incident (such as a breach or malware outbreak) is detected. Incident response involves steps like detection, containment, eradication, recovery, and lessons learned. In the context of vulnerability management, lessons learned from incidents (for example, discovering an attack succeeded via an unpatched vulnerability) feed back into improving patch management policies and faster remediation to prevent future incidents. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
IoT Security
The practice of securing Internet of Things devices (smart sensors, cameras, industrial controllers, etc.) which are often present in enterprise environments. IoT security includes managing device credentials, keeping firmware updated, and isolating these devices on separate networks. Because IoT devices can be prone to vulnerabilities and may not auto-update, organizations must include them in asset inventories and apply patches or mitigation for IoT-related CVEs to prevent them from becoming entry points for attackers.
Just-in-Time Access (JIT)
A security best practice of granting elevated permissions to users only when needed and for the shortest duration necessary. Instead of having standing administrative privileges (which could be abused if an account is compromised), JIT access ensures that powerful credentials are active only on-demand. This reduces the window of opportunity for attackers – even if a vulnerability exists or malware strikes, limited access means less chance to leverage it, aligning with the principle of least privilege.
KPI (Key Performance Indicator)
A measurable value that indicates how effectively an organization is achieving key objectives. In cybersecurity and IT management, KPIs could include metrics like the number of vulnerabilities remediated within SLA, average time to patch critical systems, or compliance score. Tracking KPIs for vulnerability management (such as patch deployment speed or reduction in open vulnerabilities over time) helps security teams and executives gauge the success of their programs and identify areas for improvement.
Kubernetes Security
The practice of protecting Kubernetes clusters (containers orchestration platforms) and the cloud-native applications they run. Kubernetes security involves regularly updating the Kubernetes software itself, scanning container images for vulnerabilities, applying network policies to limit communication, and managing secrets and permissions carefully. As containers and microservices proliferate, ensuring a secure configuration and prompt patching of Kubernetes components is vital to prevent breaches in modern application environments.
Least Privilege
A fundamental security principle that users and processes should be given the minimum levels of access – or permissions – necessary to perform their duties. Enforcing least privilege (via careful user account management and privilege restrictions) limits the damage that can be done if a vulnerability is exploited or an account is compromised. For example, running services with non-administrative accounts and giving admins standard user accounts for daily tasks helps contain potential breaches.
Legacy Systems
Older hardware or software platforms that remain in use but may no longer receive vendor support or updates. Legacy systems often run outdated operating systems or applications that have unpatched vulnerabilities, making them attractive targets for attackers. Organizations need strategies (like network isolation, virtual patching, or upgrade plans) to manage legacy system risks, since replacing them might be costly or complex but ignoring their security can lead to incidents.
MFA (Multi-Factor Authentication)
An authentication method that requires users to provide two or more verification factors to gain access to an account (for example, something you know like a password, and something you have like a mobile OTP token). MFA significantly enhances account security by making it much harder for attackers to use stolen credentials. While MFA doesn’t eliminate software vulnerabilities, it can prevent unauthorized access even if a system vulnerability exposes a password or if an attacker tries to log in to a critical system.
MTTR (Mean Time to Remediate)
A metric that measures the average time taken to fix a detected issue (such as a vulnerability) from the moment of discovery to complete remediation. In vulnerability management, a shorter MTTR for critical vulnerabilities indicates an efficient remediation process. Organizations often track MTTR as a KPI to evaluate their patch management performance, with goals to reduce this time so that security gaps are closed as quickly as possible, limiting exposure to potential attacks. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Misconfiguration
A security risk arising from incorrect or suboptimal configuration of software or hardware (e.g. open S3 buckets, default settings left enabled, or improper access control settings). Misconfigurations are as dangerous as known software vulnerabilities because they can provide an easy path for attackers. Regular configuration audits and compliance scans help catch misconfigurations, and fixing them (hardening) is a key part of remediation to bolster an organization’s security posture. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Mitigation
A defensive action or control that reduces the impact or likelihood of a security vulnerability being exploited, without completely eliminating the underlying flaw. Mitigations can include workarounds like disabling a vulnerable feature, adding a firewall rule, or enabling an intrusion prevention signature. In practice, mitigation is used when a patch is not yet available or cannot be immediately applied; it buys time by lowering risk until a full remediation (patch or permanent fix) can be implemented. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
NAC (Network Access Control)
A security solution that manages how devices access a network based on their compliance with security policies. NAC systems can enforce checks (for example, ensuring a device has up-to-date patches, antivirus, and proper credentials) before allowing network access. If a device fails the check (say it’s missing critical updates), NAC can quarantine or block it, thus preventing vulnerable or compromised machines from exposing the rest of the network to threats.
NIST
The National Institute of Standards and Technology, a U.S. agency that develops cybersecurity standards and guidelines. NIST is known for frameworks like the NIST Cybersecurity Framework and special publications (e.g. NIST SP 800-53) that provide best practices. In vulnerability management, NIST contributions include methodologies for risk assessment and recommended controls; organizations often align their security programs (including patch management, continuous monitoring, and incident response) with NIST guidelines to ensure a robust defense and compliance with federal standards.
NVD (National Vulnerability Database)
A U.S. government repository of vulnerability information, maintained by NIST. The NVD includes a catalog of CVEs along with their CVSS scores, impact ratings, and fix information. Security teams use the NVD to research vulnerabilities affecting their software stack, retrieve severity scores, and find remediation guidance. Many vulnerability scanning tools sync with the NVD to ensure they are up-to-date on the latest disclosed vulnerabilities and scoring for prioritization. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Network Segmentation
The practice of dividing a computer network into smaller segments or zones, each isolated by firewalls or access controls. Segmentation limits the spread of malware or attackers; even if one segment is compromised via a vulnerability exploit, other segments remain protected. For example, separating IoT devices or legacy systems into their own VLAN with restricted access can contain potential breaches and reduce the scope of vulnerability impact in an enterprise environment.
OWASP Top 10
A list of the ten most critical web application security risks, published by the Open Web Application Security Project (OWASP). It includes common vulnerabilities like injection flaws, broken access control, and insecure deserialization. Developers and security analysts use the OWASP Top 10 as a guide to prevent and remediate vulnerabilities in web apps. While not directly a patch management list, it influences secure coding and vulnerability scanning efforts by highlighting areas (such as XSS or SQL injection) that must be checked and fixed during application development and maintenance.
Operational Technology (OT) Security
The practice of securing industrial control systems, SCADA systems, and other hardware/software that manage physical processes (power plants, manufacturing lines, etc.). OT security focuses on ensuring these mission-critical systems are protected from cyber threats and vulnerabilities, despite often using specialized or legacy technology. Patch management in OT environments can be challenging due to uptime requirements and proprietary systems, so companies use risk-based strategies, network isolation, and sometimes “patchless” mitigations to defend OT infrastructure without disrupting operations.
PCI DSS
The Payment Card Industry Data Security Standard, a set of security requirements for organizations that handle credit and debit card information. PCI DSS mandates strict vulnerability management practices: companies must regularly scan for vulnerabilities, apply critical patches within a defined timeframe, and maintain an inventory of system components. Compliance with PCI DSS helps ensure that systems involved in payment processing are secure from known exploits, thereby protecting cardholder data from breaches.
Patch
A software update that fixes bugs or security vulnerabilities in an application, operating system, or device. Vendors release patches (sometimes called updates, fixes, or security patches) to address known issues like CVEs. Applying patches promptly is one of the most effective ways to protect systems, as it closes the loopholes that attackers might exploit. Patches can be delivered individually, as part of service packs, or cumulative updates, and should be tested and deployed regularly in any robust cybersecurity program. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Patch Management
The organized process of acquiring, testing, and deploying software patches to systems in a timely manner. Effective patch management ensures that operating systems, applications, and firmware are kept up-to-date with the latest security fixes, minimizing exposure to known vulnerabilities. This process involves prioritizing patches (for example, addressing critical CVEs first), scheduling deployments (often via automation or patch management tools), and verifying that patches have been applied successfully across all assets. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Patch Tuesday
The unofficial name for the scheduled release of patches by Microsoft (and coincidentally others) on the second Tuesday of each month. On Patch Tuesday, Microsoft publishes security updates for Windows, Office, and other products addressing recently discovered vulnerabilities. IT teams worldwide gear up on these days to evaluate and apply the patches as part of their patch management routine. While Patch Tuesday regularizes updates, critical out-of-band patches may still occur for zero-days or emergencies, and organizations need to be prepared to act on those as well. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Patchless Protection
A defensive technology that shields software from exploitation without requiring the official vendor patch to be installed. Patchless protection (pioneered by platforms like Vicarius vRx) works by applying in-memory protections or behavioral guards to block attack vectors on a vulnerable application. This approach secures applications during the gap between vulnerability disclosure and patch deployment, enabling organizations to protect critical systems against zero-days or delayed patches while maintaining normal operations. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Penetration Testing
A proactive security exercise where ethical hackers simulate attacks on a system, network, or application to find vulnerabilities that could be exploited. Unlike automated vulnerability scans, penetration testing involves creative, manual techniques to uncover complex security weaknesses or chaining of exploits. The findings from a pen test provide insight into which vulnerabilities are most dangerous in context, allowing organizations to prioritize patching and remediation efforts for issues that an attacker could realistically leverage to compromise assets.
Preemptive Exposure Management (PEM)
Definition: Preemptive Exposure Management (PEM) is a proactive cybersecurity strategy that focuses on continuously discovering vulnerabilities, validating their risk in context, and closing them automatically, before attackers can exploit them. It enables organizations to shrink the exposure window and shift from reactive patching to automated, real-time mitigation.
Core Components of PEM:
- Continuous Discovery: Real-time inventory and monitoring of all assets including traditional, cloud, and shadow IT to eliminate blind spots.
- Risk-Based Prioritization and Validation: Determines which exposures pose real threats based on context, reachability, and business impact.
- Automated Mitigation: Uses patch automation, configuration management, and orchestrated controls to close risks quickly and at scale.
- AI-Augmented Execution: Employs machine learning to predict likely attack paths and streamline remediation workflows.
Strategic Value:
PEM extends Continuous Threat Exposure Management (CTEM) by serving as its automation and execution engine. While CTEM provides the governance and process framework, PEM accelerates each stage especially post-prioritization by removing human latency from the remediation loop.
Key Benefits when adopting PEM:
- Reduces Mean Time to Remediate (MTTR) for critical exposures
- Increases automation coverage across the vulnerability lifecycle
- Improves security posture and reduces audit and incident costs
- Aligns with emerging Gartner guidance and industry best practices
Looking ahead:
As adversaries leverage generative AI to scale attacks, Preemptive Exposure Management positions defenders to respond at machine speed. Forward-thinking organizations are already seeing up to 80% faster vulnerability resolution and fewer downstream incidents by embedding PEM into their operational model.
Prioritization
In vulnerability management, the process of ranking security issues in order of importance or risk so that limited resources address the most critical items first. Prioritization typically considers factors like severity (CVSS score), asset value (is the system mission-critical or internet-facing?), and exploit availability. By using a risk-based prioritization approach, IT teams ensure that high-impact vulnerabilities (for example, a critical RCE on a server) are remediated before lower-risk issues, thereby reducing the organization’s overall risk more effectively. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Privilege Escalation
A type of attack or vulnerability whereby a user gains higher access rights than intended. For instance, a normal user exploiting a flaw to obtain admin-level privileges on a system. Privilege escalation vulnerabilities are dangerous because they can turn a minor breach into a complete system takeover. Patching privilege escalation flaws (often in operating system components or services) is essential, and implementing least privilege plus user account control can limit the potential for such exploits by restricting what any given account can do on a system.
Quarantine
In cybersecurity, isolating a device, file, or network segment to prevent the spread of potential threats. For endpoint protection, quarantine might refer to moving infected files to a safe location. In network terms, a non-compliant or compromised device can be placed in a quarantine VLAN with no access to critical resources until it’s remediated (for example, patched or cleaned). Quarantine is a containment strategy used alongside patch management: if a machine is found vulnerable and exhibiting suspicious behavior, isolating it buys time to apply patches or fixes without risking the rest of the environment.
RBAC (Role-Based Access Control)
A method for regulating access to systems and data based on the roles of individual users within an organization. In RBAC, permissions are not assigned to each user directly, but rather to roles (jobs functions like “Database Administrator” or “Helpdesk Technician”), and users are assigned those roles. This simplifies user management and enforces least privilege, ensuring people only have the access needed for their role. Proper RBAC implementation means even if certain accounts or endpoints are compromised, the damage is contained by limited permissions, complementing other security measures like patching and network segmentation.
RBVM (Risk-Based Vulnerability Management)
A strategic approach to handling vulnerabilities by focusing on the context and risk each vulnerability poses to the specific organization, rather than just the technical severity. Risk-based vulnerability management takes into account factors like exploit availability, current attacker activity (threat intelligence), and the importance of the affected asset. This means two organizations might prioritize differently even on the same CVE. RBVM drives smarter patch management ensuring that the vulnerabilities that could cause the most harm to the business are remediated first, sometimes ahead of schedule, while lower-risk issues are handled in routine cycles.
RCE (Remote Code Execution)
A critical class of vulnerability that allows an attacker to remotely run arbitrary code on a target system without authorization. RCE vulnerabilities (often stemming from issues like buffer overflows or deserialization bugs) can lead to full system compromise. Because of their severity, RCE flaws are typically rated Critical and should be patched immediately. If an RCE is being actively exploited (a zero-day), organizations may need to implement temporary mitigations or patchless protection to shield systems until an official fix is applied.
Ransomware
A type of malicious software that encrypts an organization’s data or locks systems, demanding a ransom payment for restoration. Ransomware often exploits unpatched vulnerabilities or insecure configurations to infiltrate systems. A strong patch management practice is one of the best defenses against ransomware, as closing known security holes can prevent the initial infection vector. Additionally, regular data backups and incident response plans are critical so that if ransomware strikes, an organization can recover without yielding to extortion. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Remediation
The act of correcting or fixing a security problem, often by applying a patch or making a configuration change. In vulnerability management, remediation is the end-goal – it encompasses all steps taken to eliminate a vulnerability from the environment. This could mean deploying a vendor patch, disabling a vulnerable service, updating firewall rules, or any combination of actions that removes or neutralizes the risk. Effective remediation processes ensure that once vulnerabilities are found (via scanning or testing), they are systematically fixed and verified across all affected assets. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Reporting
The process of compiling and presenting data on vulnerabilities, patch compliance, and overall security posture to stakeholders. Good security reporting can include dashboards and detailed reports that show metrics such as number of vulnerabilities by severity, patch status across systems, trends over time, and compliance with policies or SLAs. Comprehensive reporting (often facilitated by tools like vAnalyzer or other BI platforms) enables security teams, executives, and auditors to understand the effectiveness of the vulnerability management program and helps demonstrate due diligence for regulatory requirements. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Risk Assessment
The process of identifying assets, threats, and vulnerabilities, then evaluating the potential impact (risk) if those vulnerabilities were exploited. In practice, a risk assessment might involve reviewing an inventory of systems, identifying what vulnerabilities exist (via scanning results and threat intelligence), and determining the likelihood and impact of an exploit. This assessment guides decision-making by highlighting which risks are unacceptable and need mitigation (like patching a critical server or adding additional controls) versus those that might be accepted or deferred due to low impact. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Risk Management
A broader organizational process of identifying, assessing, and taking steps to minimize risks to an acceptable level. In cybersecurity, risk management involves prioritizing security efforts (such as patching, network controls, user training) based on the business impact of potential threats. The outcome could include accepting some low-level risks, transferring risk (buying cyber insurance), mitigating risk (through patches, firewalls, backups), or avoiding risk (not using a high-risk system). A mature risk management program continuously monitors the threat landscape and adjusts security controls including the vulnerability management strategy to protect key business processes and data. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
SBOM (Software Bill of Materials)
An inventory list of all components, libraries, and modules (including open-source software) that make up a codebase or application. SBOMs are becoming essential for security and compliance; they allow organizations to quickly identify if a newly announced vulnerability (e.g. a flaw in a popular open-source library) is present in any of their applications. By maintaining an SBOM, teams gain visibility into their software supply chain and can automate vulnerability scanning for all components, ensuring timely patching or updating of any insecure libraries.
SQL Injection
A web application vulnerability that allows an attacker to interfere with the queries an application makes to its database by injecting malicious SQL code. Successful SQL injection attacks can result in unauthorized data access, data loss, or corruption, and sometimes full system compromise. Preventing SQL injection involves coding best practices (like input validation and use of parameterized queries) as well as keeping web application frameworks and database software patched. Security teams often include SQL injection tests in their scanning and pen testing routines, as it remains a prevalent risk in the OWASP Top 10 list of web vulnerabilities.
Scripting
Using scripts (PowerShell, Python, Bash, etc.) to automate tasks or execute custom actions on systems. In the context of security operations, scripting is a powerful tool for automating remediation steps, deploying patches, or gathering system information. Modern vulnerability remediation platforms often include a scripting engine, allowing security teams to create custom scripts to fix vulnerabilities or misconfigurations at scale (for example, a script to uninstall a vulnerable application or adjust a registry setting on all affected machines). Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Security Analysis
The practice of examining systems, networks, or application code to identify weaknesses, threats, and improvement opportunities. A security analysis might involve reviewing vulnerability scan results, penetration testing outcomes, or configuration states to determine where the biggest risks lie. For enterprise security teams, this analysis helps in decision-making such as which vulnerabilities to remediate first or which security controls to implement next and it often feeds into compliance audits and strategic planning by highlighting the current security posture.
Security Posture
The overall security status of an organization’s networks, information, and systems based on the strength of its controls and the current vulnerability landscape. Security posture encompasses not just the presence of vulnerabilities, but also the effectiveness of defenses (like firewalls, endpoint protection, and incident response readiness). A strong security posture means that an organization has relatively few weaknesses (vulnerabilities are minimized through patching and hardening) and is well-prepared to detect and handle threats. Continuous monitoring and periodic assessments are used to evaluate and improve security posture over time. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Service Level Agreement (SLA)
A formal commitment or contract that defines the level of service expected from a provider or internal process, often including metrics and timelines. In vulnerability management and IT operations, SLAs may define how quickly critical patches must be applied (e.g. “apply critical security updates within 14 days of release”) or how soon vulnerabilities should be addressed based on severity. Adhering to SLAs is important for compliance and for managing expectations between IT/security teams and management; falling behind on patch SLAs can indicate increased risk and may require escalation or additional resources.
Supply Chain Attack
A type of cyberattack that targets less-secure elements in an organization’s supply chain to compromise a final target. This could involve tampering with hardware or software components before they reach the target environment (as seen in certain high-profile breaches where attackers inserted backdoors in software updates or open-source libraries). Defending against supply chain attacks requires verifying the integrity of software (via code signing and vetting suppliers), maintaining SBOMs to track components, and promptly applying patches when a third-party product announces a vulnerability. By understanding and monitoring the supply chain, organizations can reduce the risk of an attacker exploiting a trust relationship to introduce malicious code.
Third-Party Software
Any software application or library developed by an external vendor, used within an organization’s IT environment. Examples include PDF readers, web browsers, CRM systems, or open-source components integrated into projects. Third-party software often introduces additional vulnerabilities that the organization must monitor and patch (beyond the operating system’s native updates). A comprehensive patch management program covers third-party patching – ensuring applications like Java, Adobe products, or open-source frameworks are kept up-to-date – since attackers frequently exploit unpatched third-party apps to gain entry into corporate systems. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Threat Intelligence
Information about current and emerging cyber threats, including vulnerabilities being actively exploited, hacker group tactics, malware indicators, and exploit kits. Integrating threat intelligence into vulnerability management helps organizations prioritize patches based on real-world risks (for example, if threat intel reports a specific CVE is being leveraged in ransomware attacks, that patch gets highest priority). Threat intelligence feeds can also provide early warning of zero-day vulnerabilities, allowing security teams to implement interim mitigations while awaiting patches.
Ticketing System
A software platform (such as JIRA, ServiceNow, or an ITSM tool) used to track and manage tasks, issues, or incidents through a workflow. In the context of vulnerability remediation, a ticketing system can automatically generate tickets for detected vulnerabilities or needed patches, assign them to the responsible IT owners, and track progress. Integrating vulnerability scanners or management tools with a ticketing system ensures accountability and traceability: each vulnerability is recorded as a “ticket” and goes through verification once the patch is applied, helping large organizations systematically remediate issues and document the actions taken for audit purposes.
Unpatched Vulnerability
A security flaw in software or firmware for which a patch exists but has not yet been applied to a given system. Unpatched vulnerabilities are prime targets for attackers, as they represent known weaknesses with available exploits. The period during which a system remains unpatched (often due to testing delays, oversight, or incompatible legacy systems) is a window of exposure. Closing that window quickly by applying patches or other mitigations is a core objective of vulnerability management to reduce the risk of compromise. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Update Management
A broader term for the process of controlling the deployment of software updates (which can include feature enhancements, bug fixes, and security patches) across an IT environment. Update management overlaps with patch management but may also encompass non-security updates and version upgrades. For enterprise IT, having a structured update management program means scheduling regular maintenance, using tools to push updates, verifying success, and ensuring compatibility – all while maintaining security. This keeps systems current, stable, and less susceptible to known issues, thereby supporting both operational continuity and cybersecurity.
User Management
The administration of user accounts, credentials, and roles within IT systems or applications. Effective user management ensures that accounts are created, modified, or removed in alignment with personnel changes and that each user has appropriate access rights. In a vulnerability management platform (such as Vicarius’s vRx), user management also means inviting team members and assigning them roles (operator, admin, auditor, etc.) with defined permissions. This allows for collaboration across security and IT teams while enforcing separation of duties and least privilege principles, so that no single user account becomes a needless security risk.
Virtual Patching
A security technique that involves deploying protective measures (can be at the network, host level, or memory) to block exploitation of a vulnerability without actually installing the vendor’s official patch. Examples include using a web application firewall (WAF) to filter out malicious payloads targeting a known web app flaw or an IPS rule to drop traffic exploiting a specific CVE. Vicarius takes this further by applying in-memory protection directly on endpoints through its agent-based platform, deploying runtime-level traps and binary-level mitigations to block exploitation attempts without system downtime or dependency on third-party tools. Virtual patching is especially useful when a patch is not yet available or cannot be applied immediately – it reduces risk by providing a temporary shield around the vulnerability until permanent remediation can occur. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Vulnerability
A weakness or flaw in software, hardware, or organizational processes that could be exploited to violate security policy (resulting in unauthorized access, data leakage, or other harm). Vulnerabilities can arise from coding errors, design oversights, or misconfigurations and are typically identified by CVE entries in the cybersecurity context. Managing vulnerabilities involves scanning to discover them, assessing the risk they pose, and then remediating through patches or other controls to prevent attackers from exploiting these weaknesses. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Vulnerability Assessment
A systematic examination of an IT environment to identify security weaknesses. This typically involves using automated vulnerability scanners (and sometimes manual techniques) to find known vulnerabilities on systems, applications, and network devices. The result of a vulnerability assessment is a report detailing each discovered issue (often mapped to CVEs and severity levels). It provides a baseline for organizations to understand their exposure and plan remediation. Unlike a penetration test, a vulnerability assessment usually does not involve exploiting the findings; it is focused on discovery and evaluation of vulnerabilities. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Vulnerability Disclosure
The process of reporting and publicizing a security vulnerability. Disclosure can be coordinated (responsible) – where a researcher privately informs the software vendor, gives them time to develop a patch, and then the issue is publicly announced (often with a CVE) alongside the fix. In some cases, disclosure may be immediate or even accidental (as in the case of a leak). From an enterprise perspective, being aware of new vulnerability disclosures is critical; once a vulnerability is public, the race is on to patch systems before attackers start targeting it en masse.
Vulnerability Management
An ongoing cybersecurity practice that involves identifying, classifying, prioritizing, remediating, and mitigating software vulnerabilities. A robust vulnerability management program includes regular scanning or monitoring for new threats, prompt patch management, and verification that vulnerabilities have been addressed across all assets. It often integrates with configuration management and incident management processes. The goal is to reduce the organization’s risk by continuously keeping ahead of vulnerabilities – knowing what’s in the environment, what’s at risk, and taking swift action to fix issues before they can be exploited by adversaries. Want to see how it works for yourself? Speak to us about a demo of the Vicarius remediation first platform
Vulnerability Scanning
What is vulnerability scanning:
Vulnerability scanning is an automated process that identifies known security weaknesses, misconfigurations, and outdated software across an organization’s systems, networks, and applications. It compares assets against databases like the CVE (Common Vulnerabilities and Exposures) list to detect potential entry points for attackers.
Why It Matters:
Vulnerability scanning is a foundational cybersecurity practice that helps IT and security teams find and assess known risks before they can be exploited. It supports patch management, compliance requirements (e.g., PCI DSS, HIPAA), and ongoing risk reduction by revealing gaps in system defenses.
Types of Vulnerability Scanning:
- Network-based scanning – Scans devices across a network to detect open ports, services, and vulnerabilities.
- Host-based scanning – Analyzes individual devices or servers for configuration flaws or outdated software.
- Web application scanning – Identifies issues in websites or web apps, such as SQL injection or XSS.
- Authenticated vs. unauthenticated scanning – Scans with or without login credentials, affecting depth and accuracy.
Limitations:
While essential, vulnerability scanning is a point-in-time assessment. It often lacks real-world context, generates high volumes of findings, and can miss misconfigurations, unknown assets, or identity-related risks. Scanning alone does not prioritize by business impact or automate remediation.
Related Terms:
Exposure Management
CVE (Common Vulnerabilities and Exposures)
Patch Management
Vulnerability Assessment
Continuous Threat Exposure Management (CTEM)
Best Practices for Vulnerability Scanning:
- Scan Continuously, Not Just Periodically
Threats evolve rapidly, and assets can change daily. Schedule scans frequently, ideally daily or continuously for critical systems to avoid blind spots between scan cycles. - Use Both Authenticated and Unauthenticated Scans
Authenticated scans provide deeper visibility into software versions, configs, and missing patches. Unauthenticated scans simulate an external attacker’s view. Use both for full coverage. - Maintain an Accurate Asset Inventory
Scanning is only effective if all assets are known. Integrate with asset management tools to ensure shadow IT, cloud resources, and ephemeral systems aren’t missed. - Prioritize Findings by Risk, Not Just Severity
Don’t rely on CVSS scores alone. Prioritize based on exploitability (e.g., EPSS, KEV), asset criticality, threat intelligence, and whether the vulnerability is being actively exploited. - Integrate with Patch Management and Ticketing Tools
Automate remediation by pushing findings into IT workflows or patching tools. This reduces mean-time-to-remediate (MTTR) and improves operational efficiency. - Validate and Track Remediation Progress
Confirm that fixes are applied and exposures are closed. Track metrics like vulnerability dwell time and risk reduction trends over time. - Limit False Positives and Tune Scan Policies
Regularly refine scan configurations to minimize noise. Customize scanning templates per environment (e.g., dev vs. prod) to avoid irrelevant results. - Ensure Compliance Alignment
Map scan schedules and reporting to regulatory frameworks (e.g., PCI DSS, NIST, ISO 27001) to meet audit requirements and maintain documentation. - Embed Scanning into DevSecOps Pipelines
For modern environments, include vulnerability scanning in CI/CD workflows to catch issues early in development—especially in containers and infrastructure as code. - Use Scanning as a Component of Exposure Management
Vulnerability scanning should feed into a broader exposure management strategy that includes real-time monitoring, risk-based prioritization, and automated response. This ensures findings are not only detected but triaged and resolved in context.
WAF (Web Application Firewall)
A security solution that filters and monitors HTTP/S traffic between a web application and the internet, protecting against attacks like SQL injection, cross-site scripting, and other OWASP Top 10 threats. By inspecting web requests, a WAF can virtually patch application vulnerabilities by blocking malicious payloads even if the underlying app has not been fixed yet. This is particularly useful when immediate code changes are not possible – the WAF serves as a shield for web apps, allowing businesses to operate safely while developers work on a permanent fix.
WSUS (Windows Server Update Services)
A Microsoft server role that helps administrators manage and distribute Windows updates within an organization. WSUS allows IT teams to centralize the downloading of patches for Windows and Microsoft products, test them, and approve or deny their deployment to groups of machines. By using WSUS (or similar enterprise patch management tools), organizations ensure that all Windows systems receive critical and security updates in a timely, controlled manner, even if they don’t have direct internet access. It also provides reporting on update compliance, aiding in audit and compliance efforts.
Whitelist (Allowlist)
A security approach where only pre-approved applications, IP addresses, or entities are allowed, and everything else is denied by default (contrasting with a blacklist which blocks specific known bad items). Application whitelisting, for example, permits only trusted programs to execute on a system, greatly reducing the risk of malware or unauthorized software (even if a vulnerability exists, unapproved exploit code would be blocked from running). Many organizations adopt “allowlist” terminology and techniques to enforce strict control, ensuring that only vetted, up-to-date software is present in the environment as part of their defense-in-depth strategy.
Workaround
A temporary solution or technique that reduces the risk from a vulnerability without fully resolving it. Workarounds are often used when a patch is not yet available or cannot be applied immediately. For example, disabling a vulnerable service, closing a specific port, or editing a configuration file to turn off a feature can serve as a workaround to prevent exploitation. While workarounds can be effective in the short term, they may impact functionality, and they should be replaced by a proper fix (patch or update) as soon as possible. Documentation of workarounds is also important for compliance and future remediation tracking.
XSS (Cross-Site Scripting)
A web security vulnerability that enables an attacker to inject malicious scripts into content that other users view. In a classic XSS attack, a victim’s browser executes attacker-supplied code (often JavaScript) because an application did not properly sanitize input. This can lead to session hijacking, defacement, or redirecting users to malicious sites. Defending against XSS involves input validation, output encoding, and keeping web frameworks updated. Security teams include XSS in their testing routines and ensure developers are aware of secure coding practices to eliminate this common flaw, which is featured in the OWASP Top 10 list.


.avif)







