
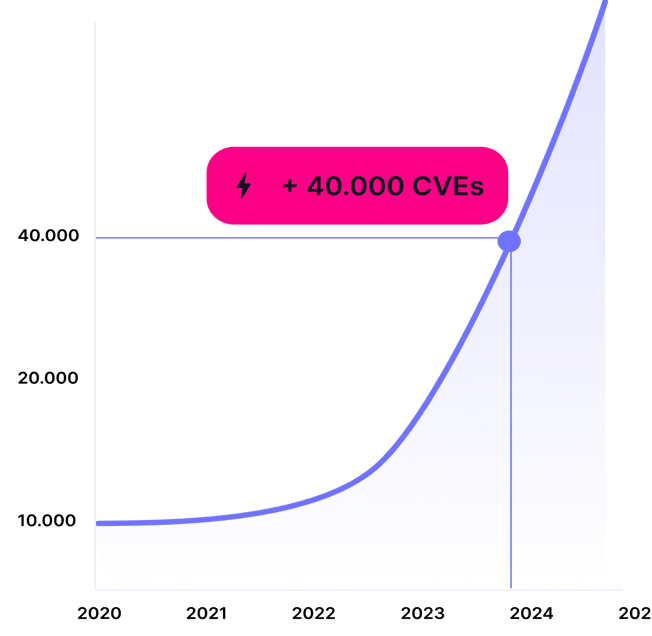
Vulnerability management has become essential as disclosed vulnerabilities surge. In 2024 more than 40 000 CVEs were published, up from about 28,961 in 2023.
Traditional scans are no longer enough; organizations need vulnerability management programs that integrate continuous monitoring, vulnerability scanning and risk based prioritization. Attackers exploit new issues within days. Continuous monitoring and vulnerability scanning find gaps as they emerge, while risk based prioritization decides which to fix.
Why periodic scanning no longer works
For years, organizations approached vulnerability management with Monthly, quarterly or annual scans. It assumed vulnerability scanning once per cycle would suffice. Today, new vulnerabilities emerge every 17 minutes , and the average time-to-exploit has dropped to five days . Without continuous monitoring, adversaries can strike between assessments. Modern vulnerability scanning platforms perform near real-time assessments across on-premises and cloud environments. Automation ensures that vulnerability scanning runs whenever new assets are deployed or significant changes occur. It bridges the gap between discovery and remediation. But scanning alone isn’t enough; risk based prioritization is required to handle the flood of data.
Dealing with the overwhelming number of vulnerabilities and embracing risk based prioritization
The National Vulnerability Database now tracks more than 230 000 unique issues , and many enterprises have hundreds of thousands of known weaknesses . Vulnerability management teams cannot fix everything, which is why risk based prioritization matters. Only about 2 % of exposures lead directly to critical assets , and 75 % are dead ends. A program that simply dumps vulnerability scanning results into a ticketing system will overwhelm operations. Risk based prioritization combines vulnerability scanning data with context about asset importance, network exposure and exploitability.
Frameworks like the Exploit Prediction Scoring System supplement (EPSS) to show which findings are most likely to be weaponized. When continuous monitoring reveals a new flaw, risk based prioritization decides whether it should be fixed immediately. Modern vulnerability management tools map attack paths and correlate vulnerability scanning results with misconfigurations and identity exposures to see which chains could lead to sensitive systems. This holistic view shows why these three elements are inseparable in an effective vulnerability management program.
Continuous monitoring, automation and vulnerability management
The transition to monitoring at scale depends on automation. Manual vulnerability scanning cannot keep up with modern infrastructure. Cloud deployments, microservices and remote work expand the attack surface daily, and each new server or container introduces potential gaps. Automated scanners integrate with configuration management databases and cloud APIs to discover assets as they appear. Monitoring triggers vulnerability scanning whenever a change occurs, ensuring that new virtual machines or containers are not left unassessed.
These automated pipelines are the backbone of modern vulnerability management. They detect vulnerabilities and feed results into orchestration tools that open remediation tickets and track progress. By coupling vulnerability scanning with continuous monitoring and risk based prioritization, security teams can focus on the vulnerabilities that matter most. Research notes that automation is essential because manual processes cannot cope with the volume of threats . Through automation, vulnerability management can scale monitoring and ensure that vulnerability scanning remains effective.
Integrating continuous monitoring and exposure management
Modern attackers exploit misconfigurations, identity flaws and chained vulnerabilities. Exposure management frameworks such as Continuous Threat Exposure Management (CTEM) take a broader view. CTEM programs involve scoping, discovery, prioritization, validation and mobilization. These stages emphasize continuous monitoring and risk based prioritization beyond pure vulnerability scanning. Such programs look at misconfigured cloud storage, identity privileges and network routes as part of the attack surface. By correlating vulnerability scanning results with configuration assessments, organizations can see which issues provide direct paths to sensitive data. With continuous monitoring across vulnerabilities, misconfigurations and identities, risk based prioritization becomes more accurate, focusing on high-impact chains. The result is a more holistic vulnerability management program that aligns scanning, monitoring and prioritization with the real ways adversaries operate.
Best practices for continuous vulnerability management
To implement continuous monitoring and vulnerability management effectively, consider the following practices:
- Asset inventory - You can’t scan what you don’t know. Automated discovery integrated with continuous monitoring ensures your vulnerability scanning covers all devices and workloads.
- Adopt continuous scanning - Move from quarterly scans to ongoing assessments. Ensure continuous monitoring triggers vulnerability scanning whenever new assets appear. This should be the foundation of any vulnerability management strategy.
- Use risk based prioritization - Combine CVSS and EPSS and KEV scores with asset criticality and exploitability. Risk based prioritization helps teams focus remediation efforts on vulnerabilities that pose genuine threats, making vulnerability management more effective.
- Automate workflows - Integrate vulnerability scanning with ticketing systems so that high-priority findings are automatically assigned. Automation supports continuous monitoring and risk based prioritization, enabling teams to respond quickly .
- Incorporate exposure management - Look beyond software flaws to misconfigurations and identity issues . Exposure management provides context for risk based prioritization and ensures vulnerability management addresses the full attack surface.
- Educate users and measure performance - Human error remains a major cause of breaches . Security awareness programs should be part of vulnerability management, and metrics like mean time to remediate help fine-tune continuous monitoring and risk based prioritization.
Final Words - Modern vulnerability management requires continuous monitoring and risk based prioritization
The era of quarterly scans is over. With thousands of new vulnerabilities each year and exploits appearing within days, organizations must adopt continuous monitoring and automated vulnerability scanning. But discovery alone is insufficient. Risk based prioritization is the key to turning endless vulnerability scanning results into actionable tasks, while exposure management provides a holistic view of the attack surface. Modern vulnerability management programs rely on the synergy of continuous monitoring, vulnerability scanning and risk based prioritization. Continuous monitoring and risk based prioritization, along with scanning, remain central to modern security.
Only by combining continuous monitoring and risk based prioritization can organizations manage the deluge. By embracing automation and context, vulnerability management becomes a dynamic, continuous discipline rather than a periodic checkbox. In a world where new issues surface every 17 minutes, only continuous protection will keep organizations secure.












