
Organizations are placing a high priority on vulnerability management solutions to protect their systems. Security leaders (CISOs, CIOs, etc.) must navigate a rapidly growing security and vulnerability management market to choose the right platform.
By understanding the market’s trajectory and the must-have capabilities for 2025 and beyond, decision-makers can better evaluate options and select a solution that fits their needs.
Market Growth and Trends
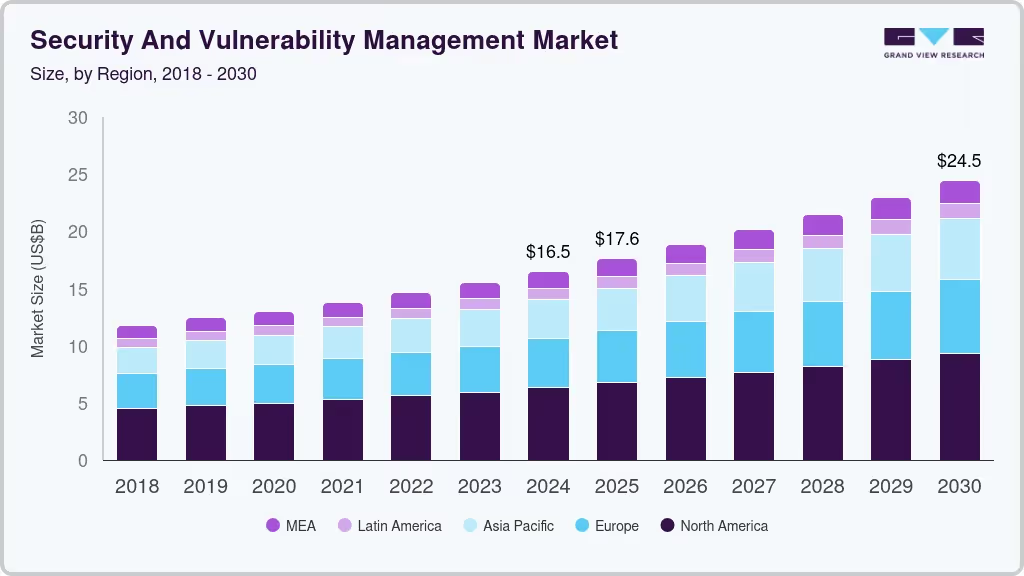
Figure: Global Security and Vulnerability Management Market size by region (2018–2030). North America leads with the largest share as of 2024. (Source)
The global security and vulnerability management market has been experiencing steady growth. It was estimated at $16.51 billion in 2024 and is projected to reach $24.47 billion by 2030, reflecting a compound annual growth rate (CAGR) of about 6.8%. This expansion is fueled by the increasing frequency and complexity of cyber threats, which are pushing organizations to prioritize robust vulnerability management solutions. In 2024, North America dominated the market with over a 37% share of global revenues , underlining the strong demand in that region. Asia-Pacific, meanwhile, is noted as the fastest-growing region for vulnerability management investments.
Several market forces converge to drive rising demand: cyber-attacks (ransomware, zero-days) are growing in sophistication; IT environments are shifting toward cloud, hybrid, and remote/BYOD models, and regulatory pressure especially in finance, healthcare, and government pushes organizations to implement vulnerability tools with strong reporting, control, and compliance assurance.
Another notable trend is the increasing adoption of cloud-based solutions for security and vulnerability management. Many organizations prefer SaaS or cloud-hosted vulnerability management platforms, which can be easier to deploy and scale. In fact, industry analysis highlights a surge in demand for integrated vulnerability management platforms, and cloud-delivered security services as key factors propelling market expansion. North America’s current lead is partly attributed to faster cloud adoption and maturity in cybersecurity practices, but other regions are catching up.
Emerging technologies like IoT and API-driven apps expand attack surfaces, demanding real-time monitoring and mitigation. Modern trends require continuous, risk-focused vulnerability management, replacing outdated periodic scanning with proactive, adaptive defense.
Must-Have Features in Vulnerability Management Solutions (2025 and Beyond)
When evaluating vulnerability management solutions, it’s critical to assess whether a given platform offers the capabilities needed to keep pace with today’s threats and IT environments. Below are key features and criteria that CISOs and security teams should look for, based on industry best practices and market trends:
- Comprehensive Asset Discovery & Inventory - Effective vulnerability management starts with knowing what you have. The solution should automatically discover and catalog all assets across your environment including on-premises servers, network devices, cloud instances, containers, mobile endpoints, and even shadow IT to ensure no asset is overlooked. By eliminating blind spots in asset inventory, you can be confident the platform’s vulnerability assessment covers your full attack surface.
- Continuous and Automated Vulnerability Scanning - Modern environments demand continuous scanning with scheduled, on-demand, and real-time monitoring across networks, apps, and cloud. Leveraging up-to-date threat intelligence ensures rapid detection of new vulnerabilities and swift organizational response.
- Risk-Based Prioritization of Vulnerabilities - Not all vulnerabilities pose equal risk. Modern platforms must prioritize critical issues using context beyond CVSS exploit likelihood, asset exposure, threat intelligence, and machine learning ensuring resources focus on high-impact gaps while minimizing wasted remediation efforts.
- Automated Remediation Workflows (Integration with Patch Management & ITSM): Identifying vulnerabilities isn’t enough remediation must be streamlined. Platforms should integrate with patch management and ITSM tools for automated or one-click fixes, ticketing, and policy-based patching. Automation reduces exposure windows, aligns with IT workflows, and minimizes manual remediation effort at scale.
- Integration with Security Ecosystem & APIs: Modern solutions must integrate with SIEM, SOAR, ITSM, and DevSecOps pipelines via APIs. Seamless integration enables correlation, automation, and embedding vulnerability management into CI/CD workflows, ensuring unified, proactive security across development and infrastructure.
- Support for Cloud and Hybrid Environments: Solutions must support hybrid multi-cloud (AWS, Azure, GCP), containers, VMs, and on-prem. Ensure scalability, flexible deployment, agent/agentless scanning, and tracking ephemeral instances for consistent vulnerability management across dynamic environments.
- Detailed Reporting and Compliance Features: Compliance reporting is critical for regulated industries. Choose platforms offering built-in reports mapped to standards (PCI-DSS, NIST, ISO, HIPAA), customizable dashboards, audit-ready summaries, remediation trails, and business risk translation supporting both technical teams and executives in proving compliance readiness.
- User-Friendly Interface and Workflow: Usability is vital in vulnerability management. Prioritize intuitive platforms with clear dashboards, role-based access, customizable views, and alerting integrations. A user-friendly interface boosts team efficiency, prevents underuse, and ensures faster response compared to cumbersome solutions with similar technical features.
Future-Focused Considerations: Automation, AI, and CTEM
Selecting a vulnerability management solution in 2025 is not just about addressing the needs of today, but also about preparing for the future. Two forward-looking aspects to consider are the use of automation/AI and alignment with emerging frameworks like Continuous Threat Exposure Management (CTEM).
Automation and AI: Top-tier vulnerability management platforms now incorporate machine learning and artificial intelligence to enhance their effectiveness. AI can help in predictive analytics forecasting which vulnerabilities are most likely to be exploited, and in automating routine tasks. For example, machine learning models can correlate vulnerability data with threat intelligence to automatically highlight the riskiest vulnerabilities, or even suggest the optimal remediation action. AI-driven risk scoring is increasingly part of risk-based vulnerability management, helping teams cut through noise and focus on what truly matters. Automation, meanwhile, extends from auto-discovery of assets to automatically applying patches or configuration changes for known issues.
Technologies like AI and ML are playing a significant role in enhancing vulnerability detection and enabling predictive analytics and automation in this field. When evaluating solutions, consider how much they leverage automation. A platform that can automatically handle certain classes of vulnerabilities or integrate with orchestration tools can significantly reduce the manual workload on your team.
Continuous Threat Exposure Management (CTEM): In response to the dynamic threat landscape, analysts (e.g. Gartner) have proposed the CTEM framework, which stands for Continuous Threat Exposure Management. CTEM is a comprehensive, programmatic approach to continuously identifying, monitoring, and remediating threats across your attack surface before attackers can exploit them. In practice, CTEM involves ongoing cycles of scoping your assets, discovering and prioritizing vulnerabilities, validating security controls, and mobilizing the organization to remediate in a continuous loop. The goal is to move from periodic assessments to a continuous improvement process in security.
When choosing a vulnerability management solution, it’s wise to favor vendors that support CTEM principles, meaning their platform facilitates continuous assessment (not just occasional scanning), provides a real-time view of your security posture, and helps prioritize and drive remediation in an iterative way. CTEM-aligned solutions often leverage threat intelligence, security monitoring data, and vulnerability management capabilities together to give you proactive insights into your risk exposure. By embracing a CTEM approach, organizations can improve cyber resilience and ensure their vulnerability management keeps up with the pace of modern threats.
Conclusion
Market trends indicate that vulnerability management is a critical and growing component of cybersecurity strategy. The right vulnerability management solution will combine comprehensive coverage (of assets and vulnerabilities) with intelligent prioritization and strong integration into your workflows.
As you evaluate options, keep in mind the must-have features discussed above: asset discovery, continuous scanning, risk-based prioritization, remediation automation, integrations, cloud/hybrid support, and compliance reporting as well as the vendor’s vision for automation and continuous exposure management. A platform that meets these criteria will enable your organization to effectively identify, assess, and remediate vulnerabilities, thereby reducing risk in an increasingly challenging threat environment.












