
Many organizations confidently point to their compliance with NIST SP 800-53 as evidence of a strong cybersecurity posture. But history has repeatedly shown that “passing the test” doesn’t guarantee real-world resilience. Despite the agency’s documented compliance, the U.S. Office of Personnel Management suffered a breach in 2015 that exposed the personal data of more than 21 million people. The SolarWinds attack in 2020 similarly demonstrated how attackers can exploit blind spots in monitoring and patching, even when formal frameworks are in place.
What these breaches reveal is a gap between what’s written and what’s real. Compliance frameworks like NIST SP 800-53 are necessary blueprints, but without continuous execution, they become hollow rituals. The controls exist in potential, but they don’t act. Exposure management addresses that gap. It’s the operational layer that keeps NIST controls alive, proactive, visible, and responsive to current threats – not historic intentions.
Why NIST SP 800-53 still matters
Originally published in 2005 under the Federal Information Security Modernization Act (FISMA), NIST SP 800-53 remains a foundational standard across both federal and private sectors despite the emergence of newer cybersecurity frameworks. The 800-53 control catalog is still core to FedRAMP authorization and widely adopted by civilian agencies, defense contractors, and commercial enterprises aiming for rigorous security governance.
Its enduring relevance stems from its extensibility and alignment. NIST SP 800-53 maps well to international standards like ISO 27001, supports modular tailoring, and underpins other frameworks like the NIST Cybersecurity Framework (CSF). For any organization with regulatory requirements, cloud adoption, or high-risk assets, it remains the control set of record.

The compliance gap
While NIST SP 800-53 provides comprehensive coverage of what organizations should do, many fall short on how and when they actually do it. This results in a state of “paper compliance” where organizations employ documented “best practice” policies that look great in audits, but which fail to translate into well-timed action. A prime example of this disconnect is highlighted by CISA’s Binding Operational Directive (BOD) 22-01, which mandates agencies to remediate Known Exploited Vulnerabilities (KEVs) on a rolling deadline. This directive clearly signals that snapshot compliance isn’t sufficient by emphasizing continuous remediation over periodic policy reviews. A vulnerability patched once a year is, after all, still potentially exploitable for the other 364 days if you don’t keep an eye on it. A pattern emerges in these environments of organizations passing audits but still being highly breach-prone because the mechanisms for actual control enforcement are missing.
Common factors in this compliance gap include:
- Policy without execution: Having a patching policy doesn’t mean patches are applied in time. Vulnerability remediation should not have to depend on human staff alone. Vulnerability exploitation at scale is a numbers game; modern criminal syndicates are extremely well-equipped to play, and they’re famous for not keeping office hours.
- Audits without assurance: Annual check-ins can’t validate daily threat defense in a world where (unrestricted hostile LLM) AI-vibe-coded software exploits are available on dark web marketplaces within literal minutes of a CVE’s publication. We live in the age of script kiddies wielding weaponized AI; annual audits present at best the illusion of safety.
- Controls without visibility: You can’t protect what you can’t see, especially in today’s often highly heterogeneous and distributed environments. The modern enterprise stack is riddled with unmanaged assets, third-party software, and that one library everyone in the world depends on that’s been maintained by that one guy since 2003 – all glued together with insecure defaults. None of which show up in the compliance binder unless (sometimes even if) you go looking.
Exposure management corrects for these limitations by ensuring that cybersecurity controls aren’t just defined but continuously enforced, monitored, and improved.
What exposure management means and why it matters
Exposure management is a proactive discipline focused on identifying, prioritizing, and mitigating exploitable risks on an ongoing basis. Far from being a replacement for frameworks like NIST SP 800-53, it’s a part of realizing them more effectively.
At its core, exposure management entails:
- Continuous asset discovery: Surface all assets, including those often-overlooked shadow IT deployments, unmanaged endpoints, and legacy or EOL systems.
- Risk-based prioritization: Go beyond CVSS scores. Prioritize vulnerabilities based on exploitability, business context, and impact to mission-critical operations.
- Automated remediation and orchestration: Fix vulnerabilities quickly through scriptable or policy-driven patching, even when vendors don’t provide timely updates.
- Compliance evidence generation: Maintain audit-ready reports and control-state visibility to satisfy frameworks like NIST, FedRAMP, and FISMA.
Exposure management platforms bring this into practice by offering live risk scoring, prioritized mitigation planning, one-click patching, and mitigation scripting. Together, these capabilities transform exposure management from concept into action and help to build an always-on defense posture that packs compliance frameworks with real operational muscle.

Mapping NIST SP 800-53 control families to exposure management
NIST SP 800-53 organizes its extensive control set into 20 distinct families. Instead of replacing these, exposure management enforces them through continuous, risk-informed, operational practices. The table below outlines how exposure management activities, such as those facilitated by platforms like vRx by Vicarius, align with and support core families within SP 800-53:
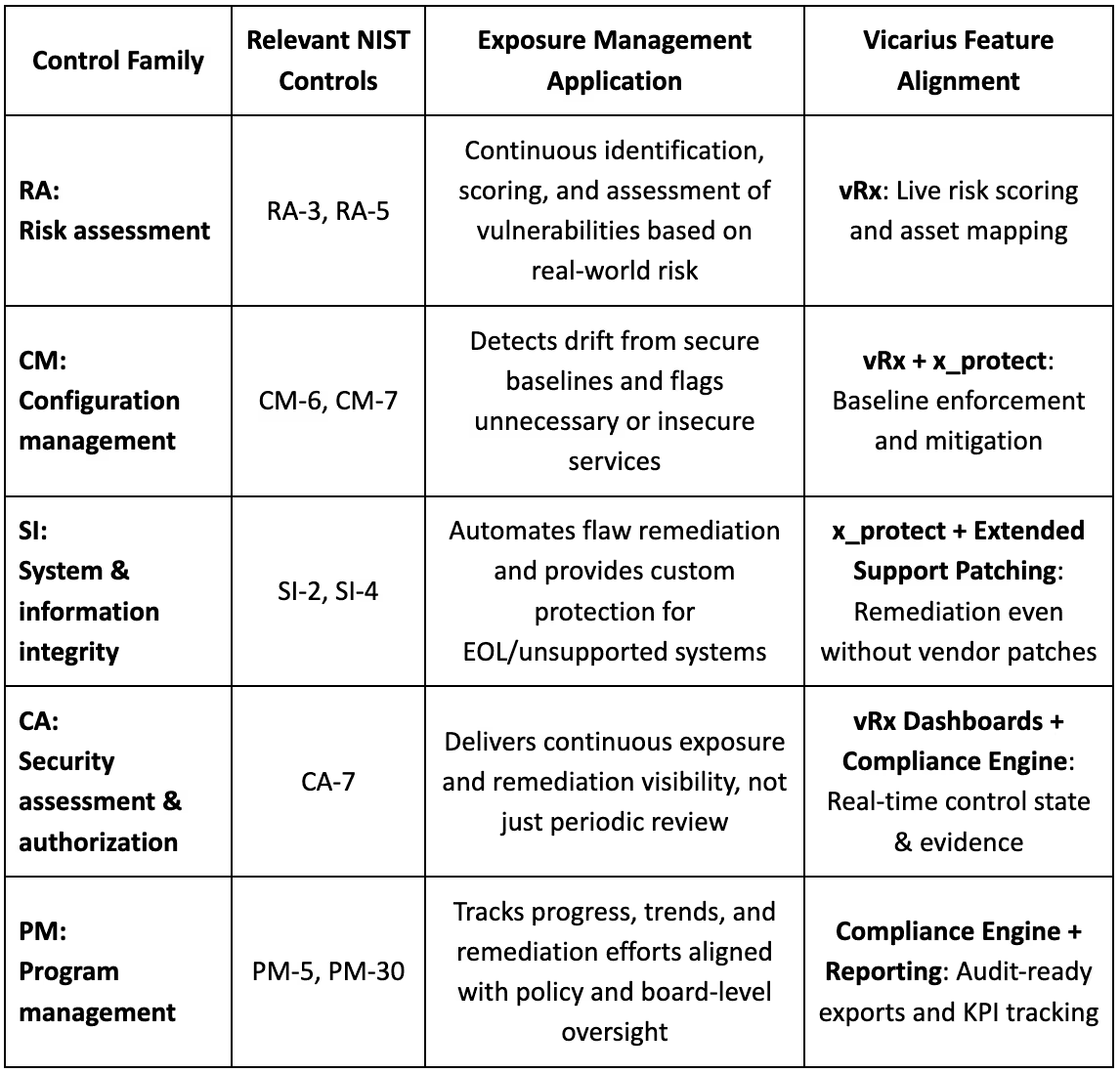
By combining cybersecurity controls and institutional experience into live, measurable action, exposure management enables real-time resilience that renders continuous compliance defensible, meaningful, eminently achievable, and ultimately sustainable.

Business and compliance value
Exposure management is where compliance, risk reduction, and executive reporting converge into concrete outcomes that matter to audits, boards, and security teams alike.
Compliance assurance becomes continuous
Controls like SI‑2 and CA‑7 are fulfilled not just in policy, but every day in practice through automated patching, continuous monitoring, and risk‑based remediation that turn audit readiness from a project into a built-in feature.
Risk reduction becomes measurable
Metrics such as Mean Time to Remediate (MTTR), rate of Known Exploited Vulnerability (KEV) closure, and declining risk scores provide data you and your leadership can act on. These aren’t just nice-to-haves, they are ongoing proof that you’ve actively reduced exploitable exposure.
Reporting becomes board‑ready
Gartner predicts that by 2026, 70% of corporate boards will include cybersecurity expertise. Exposure management gives CISOs dashboards, trend reports, and impactful visuals that let them speak board‑level fluently and help to advance the conversation from abstract policy to demonstrable outcomes.
Case example
Consider a federal contractor reliant on Windows Server 2012 for a legacy application. The OS has reached end-of-life. Per NIST SP 800-53’s SI-2, the organization is still obligated to remediate any known flaws in this system. But vendor patches are no longer available. Using vRx, the contractor discovers the exposure through risk scoring, deploys a custom mitigation using x_protect, and documents the remediation effort through the platform’s audit logs. In effect, they create a compensating control that not only reduces exploitable surface area but also meets the intent of the SI-2 requirement.
- Legacy compliance: Maintains security posture for unsupported systems.
- Audit viability: Generates reportable evidence of compensating controls.
- Operational continuity: Avoids downtime or forced migration.
Sustainable security starts with continuous enforcement
Security doesn’t come from paperwork. It comes from execution. Frameworks like NIST SP 800-53 are the foundation of defensible cybersecurity, but they’re only effective when controls are actually put into everyday practice. Exposure management breathes life into those controls. It ensures they are continuously enforced, visible to leadership, and responsive to threats. If you’re ready to move beyond checklists and into real-time, risk-based control enforcement, explore how Vicarius can help bring your exposure management to life by mapping directly to the controls you already know, and realize the protection your systems actually need. Learn more about our range of applications or book a demo today!






.avif)




