The Cyber Resilience Act (CRA) introduces mandatory cybersecurity requirements for any product with digital elements that is sold within the European Union. This includes not only traditional IT products but also connected devices, consumer electronics, and software-as-a-service offerings. This expansion of regulatory scope necessitates a reassessment of how products are secured, monitored, and maintained throughout their lifecycle. Unlike earlier frameworks that treated security as a market differentiator, however, the CRA elevates it to the level of regulated obligation.
This shift has significant consequences for product and infrastructure planning: cybersecurity must be designed into systems from the outset and maintained continuously. Organizations can no longer rely on ad hoc controls or patch-late approaches; they are expected to demonstrate security as a condition of market entry and ongoing compliance. As a result, teams are under growing pressure to deliver continuous visibility into exposures, integrate risk management across development and operations, and align closely with compliance functions.
This requires not only new tools, but new workflows and cultural expectations. Security, once treated as an external audit concern, is now a shared, embedded responsibility across the product lifecycle.
Core pillars of the Cyber Resilience Act
Lifecycle vulnerability management
The CRA requires that cybersecurity be embedded across every phase of the product lifecycle. This means secure design practices at the start, vulnerability-aware development and deployment practices, and sustained support and patching after release. For developers and product teams, it shifts the emphasis from minimum viable security toward defensible-by-default architectures and maintainable security baselines.
Compliance with the CRA depends on timely patching of known vulnerabilities, formalized coordinated vulnerability disclosure (CVD) procedures, and continuous monitoring of third-party components. Vulnerability management is no longer a reactive process; it must now operate as a documented, systematic function that keeps pace with evolving threats and software dependencies.
Risk-based product classification
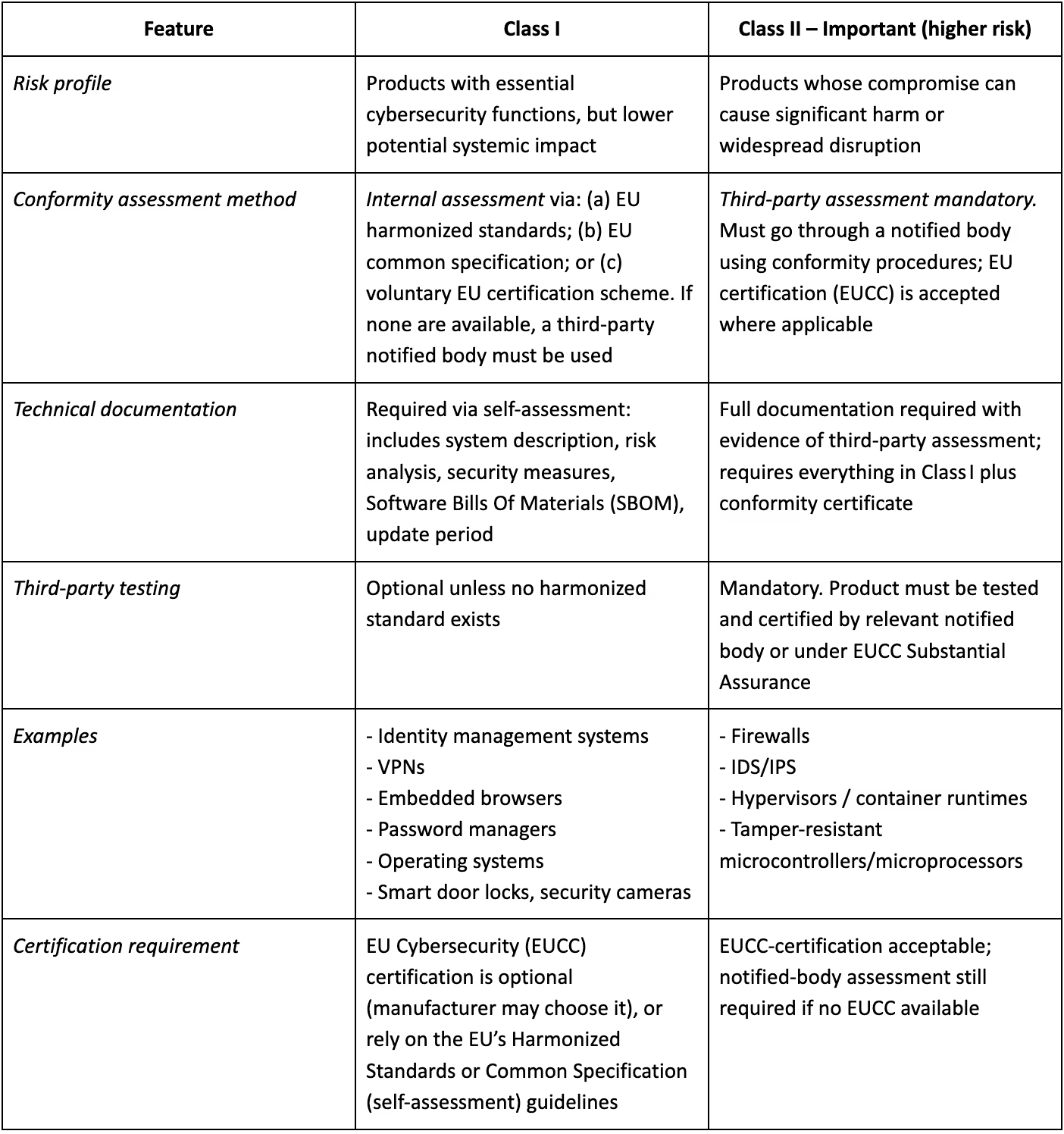
The CRA distinguishes between Class I (important) and Class II (critical) products based on their potential impact on users and infrastructure. This classification takes into account factors like whether the product is used in essential services, processes personal data, or operates in a connected or autonomous fashion. Teams need to understand which class applies to their products early in the development process to ensure the correct level of compliance is applied. Class II products face enhanced obligations, including more rigorous technical documentation, stricter conformity assessment procedures, and longer retention of compliance records.
These controls are designed to reduce systemic risk and ensure that products with broader potential impact meet higher security standards before and after market entry.
Software supply chain transparency
Software Bills of Materials (SBOMs) are now required under the CRA to provide clear, up-to-date listings of all components included in a digital product. SBOMs are essential for traceability and help teams rapidly assess exposure to newly disclosed vulnerabilities. Maintaining them demands tight coordination between developers, integrators, and third-party vendors, as well as tooling to keep them accurate across versions and releases.
Manufacturers must proactively track vulnerabilities in upstream dependencies and act to mitigate them when discovered. This involves integrating vulnerability feeds, monitoring CVE and EUVD databases, and ensuring that patching or compensating controls are applied swiftly. The CRA places responsibility on the manufacturer regardless of whether the affected component was developed in-house or supplied by a third party.
Security updates by design
The CRA stipulates that security updates must be delivered separately from functional or feature updates. This ensures that users can receive and apply critical patches without waiting for the next version release. For release managers and developers, it introduces a need for versioning strategies, signing workflows, and secure delivery mechanisms that prioritize security changes as their own category of update.
Most consumer-facing devices will be required to support automated updates by default. This reduces reliance on end-user action and helps close the window of exposure more quickly. However, it also raises concerns around user consent, firmware integrity, and rollback handling, all of which must be designed with both usability and compliance in mind.
The role of preemptive exposure management (PEM)
Continuous visibility across the attack surface
Preemptive Exposure Management (PEM) platforms provide continuous monitoring of exposures, vulnerabilities, and misconfigurations across both development and production environments. This persistent visibility enables teams to detect issues earlier and track them over time, rather than relying on periodic security assessments or ad hoc scanning.
A central goal of the CRA is lifecycle risk posture awareness, i.e., knowing the real-time security state of a product from development through operation. PEM tools support this by enabling developers and infrastructure teams to maintain live maps of known issues, remediation status, and affected systems, all of which are crucial to CRA-aligned lifecycle security management.
Automated prioritization and remediation
PEM platforms integrate with vulnerability scanners, SBOM sources, patch management systems, and scripting engines to automate the entire remediation workflow. This creates a single flow from detection to fix, reducing mean time to remediation (MTTR) and minimizing the risk of human error or backlog accumulation.
Prioritization within PEM systems is often based on exploitability, exposure, and business impact intended to assist teams to focus first on vulnerabilities that are both real-world threats and within reach of active exploitation. This aligns well with CRA’s emphasis on timely and risk-informed remediation, especially in environments with large, heterogeneous asset sets.
Oversight of third-party and open source components
PEM platforms continuously monitor third-party and open-source libraries for new vulnerabilities using live threat intelligence and vulnerability feeds. These tools help track package versions, identify known issues as they emerge, and alert teams when action is needed to mitigate the risk of inherited vulnerabilities.
By combining real-time risk scoring with contextual data - such as exploit maturity and prevalence - PEM tools allow security teams to assess and respond to third-party component vulnerabilities far more efficiently than traditional manual methods. This reduces time spent chasing low-impact issues while ensuring high-severity vulnerabilities don’t go unaddressed.
Strategic actions for security and compliance teams
- Begin with a lifecycle-aligned readiness audit: Start by mapping current vulnerability management, patch workflows, and third-party software governance against the CRA’s lifecycle and disclosure requirements. This helps surface process gaps and documentation shortfalls that may impact compliance.
- Use audit insights to close policy gaps: Identifying blind spots enables more proactive, policy-aligned practices. Benchmarking against CRA criteria supports focused improvements that reduce both compliance risk and operational debt.
- Centralize key workflows with PEM tooling: PEM tools consolidate asset discovery, scanning, prioritization, and remediation. This reduces fragmentation, eliminates tool sprawl, and prevents delays caused by missed handoffs.
- Improve response time through shared visibility: A unified exposure view strengthens coordination between IT and security teams, enabling faster, more efficient remediation and audit readiness.
- Integrate SBOM and threat intelligence into dev workflows: Incorporate SBOM tracking, threat intelligence, and OSS risk scoring directly into CI/CD pipelines. This ensures continuous feedback and better alignment with release schedules.
- Bake supply chain risk into release hygiene: Making exposure management part of your development rhythm embeds compliance into routine practices. This prevents bolt-on controls and promotes consistency across releases.
- Transition from reactive to preemptive practices: Reframing patching as a continuous quality process shifts security from firefighting to forward-planning and resilience-building.
- Instill operational resilience through continuous visibility: Continuous monitoring supports early mitigation, better audit outcomes, and sustained compliance with CRA mandates.
Conclusion & next steps
The CRA reflects a broader evolution in cybersecurity thinking, where exposure visibility and accountability are embedded from the start and persist through the entire product lifecycle. Teams must operate from the assumption that every phase is under scrutiny, as is statistically increasingly likely in the current milieu. To meet this challenge, organizations need unified workflows that integrate discovery, prioritization, remediation, and compliance reporting. This consolidation not only reduces friction between teams but also provides the traceability and audit readiness that CRA compliance demands.
vRx by Vicarius is designed to meet these needs by providing real-time discovery, risk-based prioritization, automated patching, and lightweight compliance scanning in one integrated platform. It supports vulnerability and misconfiguration management across third-party, operating system, and custom application layers.
Request a demo to see how vRx can simplify CRA compliance and exposure management in your environment while improving visibility, reducing MTTR, and supporting long-term resilience strategies.
.avif)