
Introduction
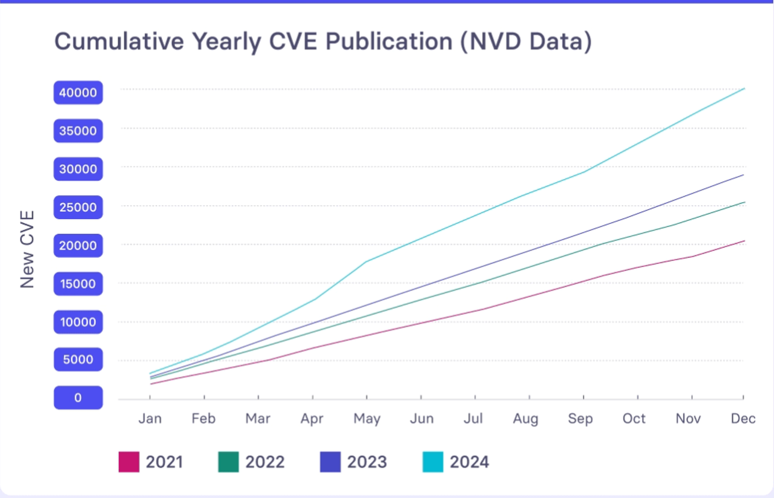
Analysts recorded more than 28,000 Common Vulnerabilities and Exposures (CVEs) published in 2023 and over 40,000 CVEs in 2024. Manual vulnerability triage can’t keep pace, and exploited vulnerabilities cause about 20 % of breaches. These overwhelming numbers demand a shift toward automated vulnerability management, a strategy that continuously detects exposures, prioritizes risks and drives auto remediation. The shift hinges on vulnerability management automation that leverages AI and automation to handle the flood of flaws and deliver proactive solutions. A line graph of annual CVE disclosures over the last decade (from NVD data) would vividly illustrate this exponential growth and underscore why automated vulnerability management and vulnerability management automation solutions are now essential.
Why Automation Is Essential
Manual patching cannot keep up with the speed at which new vulnerabilities are discovered and exploited. Forbes notes that risk-based patching and automation foster collaboration between security and IT teams, reduce human error and can slash breach rates by 80 %. Traditional vulnerability management processes are reactive teams that identify flaws, assess severity and then scramble to patch.
In contrast, automated vulnerability management platforms scan continuously, apply risk models and trigger auto remediation. This approach is at the heart of vulnerability management automation and makes AI a key ally. Such data show AI, automation and automated vulnerability management are now the baseline for robust solutions that ensure timely auto remediation and efficient vulnerability management automation.
AI-Powered Vulnerability Management
Artificial intelligence is the engine powering automated vulnerability management. Machine-learning algorithms sift through data from vulnerability scanners, asset inventories and threat feeds to prioritize remediation tasks. This type of vulnerability management automation enables real-time risk scoring and auto remediation triggers that update software or isolate systems without waiting for a human. When integrated into AI-driven security tools, automation becomes more than a process; it becomes an adaptive agent that can write patches, open pull requests or orchestrate patch deployment across thousands of assets. These solutions can quickly map the attack surface, compare exposures to exploit kits and forecast which flaws will be exploited.
By harnessing AI, automated vulnerability management delivers end-to-end solutions that transform vulnerability management automation from a manual slog into a responsive ecosystem where auto remediation is the norm. As part of vulnerability management automation, automated vulnerability management solutions deliver integrated vulnerability management automation and auto remediation that accelerate remediation and free humans to focus on higher-level tasks.
Auto Remediation: Beyond Patching
Auto remediation goes beyond deploying patches. In a fully automated vulnerability management architecture, automatic remediation is an orchestrated workflow that can disable vulnerable services, deploy configuration changes or roll back risky software versions. These solutions rely on vulnerability management automation to integrate with CI/CD pipelines, ticketing systems and cloud infrastructure. AI detects anomalies and triggers the auto remediation engine.
Forbes explains that automation reduces human error and accelerates risk mitigation, which is why auto remediation is becoming standard. If a critical vulnerability is exploited within days , automated vulnerability management combined with AI can trigger auto remediation within minutes. These solutions not only patch but also verify the outcome, creating audit trails for compliance.
Unified Solutions: The Next Phase
Modern solutions for automated vulnerability management often combine AI-powered discovery engines with policy-driven orchestration for auto remediation. This interplay of automation and intelligence is sometimes called vulnerability management automation 2.0. Traditional tools produced endless vulnerability lists; new solutions integrate contextual awareness, asset criticality and exploit likelihood.
A Hacker News article observed that manual processes cannot cope with the volume of vulnerabilities and that security teams are overwhelmed. That’s why AI-driven automated vulnerability management is so impactful: it can prioritize automatically, assign tasks and even track remediation progress. With vulnerability management automation, engineers receive fewer false positives and more actionable recommendations.
As these solutions mature, auto remediation workflows include approval steps to ensure compliance while still leveraging automation. A unified programme demonstrates how automated vulnerability management solutions and vulnerability management automation tools can unify scanning, prioritization and remediation.
Implementation Steps and Best Practices
Implementing automated vulnerability management requires careful planning and a structured roadmap. Key steps include:
- Inventory Assets: Build a comprehensive asset inventory and implement continuous scanning using vulnerability management automation platforms that ingest vulnerability data, business context and threat intelligence.
- Prioritize and Score: Use AI-driven analytics to assign risk scores and prioritize remediation. High-risk issues should be auto remediated; medium ones create tickets.
- Integrate and Orchestrate: Implement orchestration that combines detection, prioritization and auto remediation into cohesive solutions. Integrate automation with change-management systems to avoid drift.
- Align Policies: Align policies so auto remediation handles the most critical vulnerabilities while ensuring compliance and governance.
- Ensure Human Oversight: Even with AI and automation, analysts must review AI decisions to ensure ethical use and catch anomalies.
- Collaborate Across Teams: Successful vulnerability management automation depends on cross-functional collaboration across security, operations and development teams.
By following these steps, organizations can build automated vulnerability management solutions that are scalable and effective.
Challenges and Considerations
Despite its promise, automated vulnerability management poses challenges. Vulnerability management automation must include continuous testing and feedback loops to refine AI models and prevent misconfiguration. Cisco’s AI-powered Hypershield announcement illustrates this shift: patching sprawling applications is beyond manual processes, and autonomous segmentation and self-qualifying upgrades are designed to address these issues. Compounding the challenge, attackers can exploit vulnerabilities within hours while patches may take 20–45 days. These realities reinforce the need for automated vulnerability management solutions and vulnerability management automation solutions that include auto remediation and advanced automation.
Organizations must also recognize that AI models need high-quality training data and can be misled by noisy inputs. Over-reliance on auto remediation may create blind spots if exceptions aren’t monitored. Continuous human oversight and clear escalation paths remain essential. Finally, adoption can be slowed by culture: IT teams may be wary of automated vulnerability management and auto remediation breaking systems; leadership must champion the move and ensure teams trust the process.
Final words
The future of cybersecurity is inseparable from automated vulnerability management (the discipline), and the automation of vulnerability management processes that make it real. The scale of modern threats, the speed of exploitation and the complexity of software supply chains demand a proactive stance. By deploying intelligent solutions that integrate continuous scanning, predictive analytics and automatic remediation, organisations can transform their defensive posture.
For leaders seeking resilience, the message is simple: invest in AI, invest in automation, and let automated vulnerability management and auto remediation solutions drive a safer digital future. This unified vulnerability management automation approach ensures that vulnerability management automation solutions remain at the core of security.
Ultimately, automated vulnerability management and vulnerability management automation must evolve together. An effective program uses automated vulnerability management solutions and vulnerability management automation tools to unify scanning, prioritisation and remediation. Emphasising collaboration, AI, automation and solutions ensures vulnerability management automation delivers on its promise: reliable remediation at machine speed.












