
For years, security teams have operated under the crushing weight of “patching everything”, driven by the fear that ignoring the wrong vulnerability leads to catastrophe, or worse, missing their KPIs. A groundbreaking new study on medical device security published in Scientific Reports has, however, mathematically confirmed what many CISOs and sysadmins have long suspected: technical severity is not the same as actual risk.
Despite the study’s focus on the high-stakes world of healthcare, where software flaws can directly impact human life, its findings are universally applicable to IT infrastructure. The research indicates that relying solely on static scores leads to poor prioritization and operational inefficiencies, favoring an approach wherein context and threat intelligence matter far more than simply a CVSS Base Score. The core argument is that the industry's standard approach is fundamentally flawed. When organizations filter vulnerabilities through the lens of real-world "Threat" and "Environment," nearly 40% of the "Critical" backlog disappears, allowing teams to shift from a panic-driven strategy to one based on rigorous risk assessment.
The "Base Score" Trap: Your backlog is artificially growing
The Common Vulnerability Scoring System (CVSS) is the industry standard for assessing severity. According to the research, it may also inadvertently be contributing to the noise. The study analyzed the latest standard, CVSS v4.0, and found that it systematically increases the average Base Score by 0.77 points compared to its predecessor, v3.1.
This inflation occurs because Base Scores are "context-blind"; they capture only the intrinsic technical properties of a vulnerability with no regard to the specific environment in which it is deployed. If your security team relies on National Vulnerability Database (NVD) data alone, your backlog of "Critical" items is mathematically guaranteed to grow, not shrink. The researchers note that this narrow use of base scores results in "unjustified alarmism" where teams chase ghosts rather than legitimate threats. Relying on these inflated numbers creates a "boy who cried wolf" dynamic, where high vulnerability scores lose their meaning and distract from the vulnerabilities that are actually likely to impact your network most urgently.
vRx by Vicarius was built because we knew that a static number cannot represent a dynamic risk. The study confirms that Base Scores are insufficient because they ignore the reality of your infrastructure. You cannot effectively prioritize remediation based on a number that assumes the worst-case scenario for every asset, regardless of its actual exposure or importance.
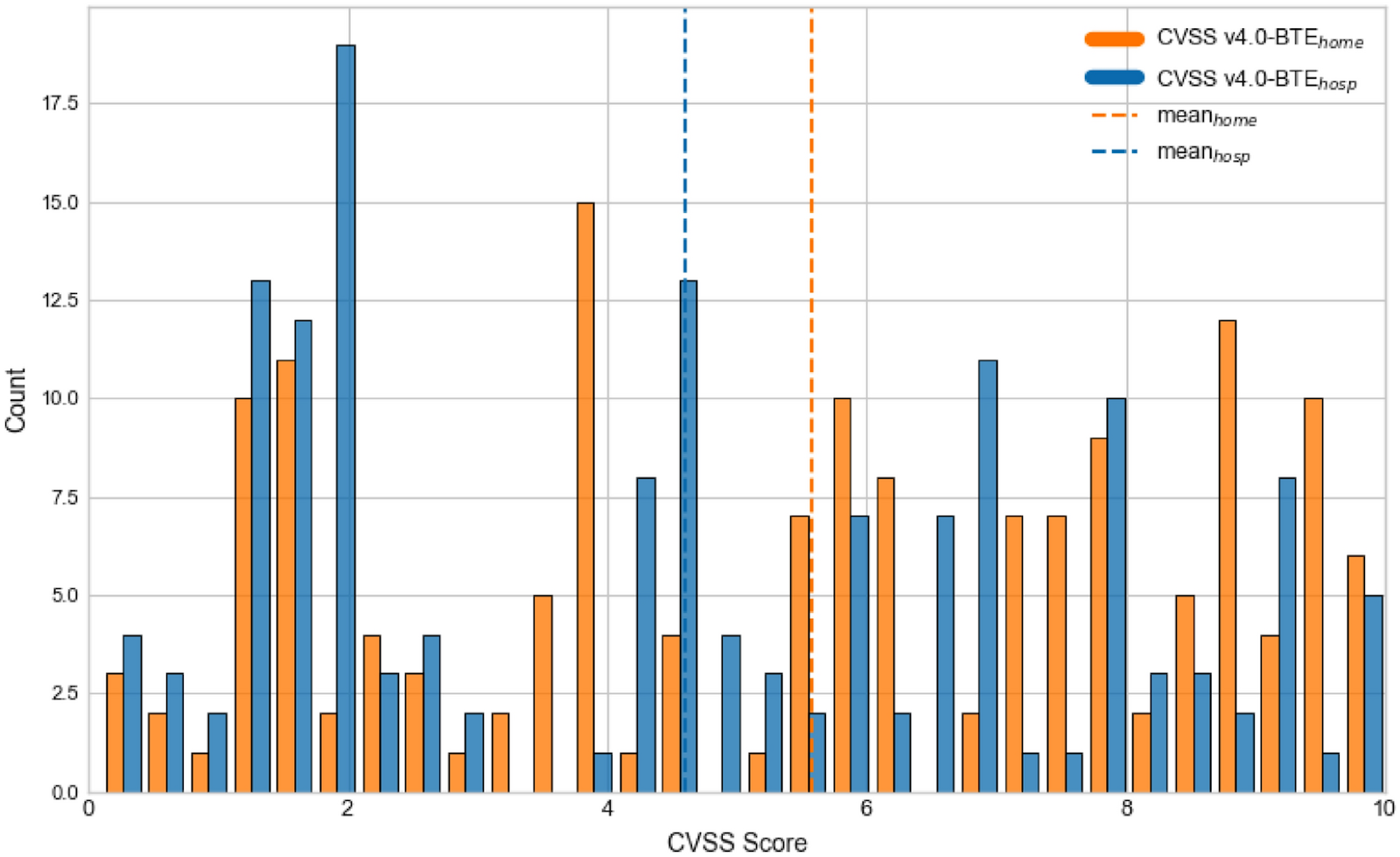
Distribution of CVSS 4.0 BTE scores computed under the two environmental profiles: “Hospital” (located at business premises, protected from greater internet by other infrastructure) and “home” (typical consumer-grade cyber protection only). (Source: ResearchGate)
Context is the Ultimate Filter
The most compelling finding of the research is the "context drop." When the researchers applied contextual factors to the vulnerability data - specifically, Environmental metrics - 36.8% of vulnerabilities rated as Critical or High dropped to Medium or Low priority. This demonstrates that over a third of the alerts keeping security teams awake at night may not even warrant getting out of bed for, so to speak, once the realities of one’s deployment environment are considered.
The hospital vs. home difference
To prove this, the study compared the exact same vulnerability in two different profiles: a controlled "Hospital" setting and an uncontrolled "Home" setting. The result was a risk score difference of 2.3 (CVSS) base points. The vulnerability was rated lower in the hospital setting because of existing defenses and professional supervision. For IT professionals, this validates the concept that an air-gapped server (Hospital) should not carry the same risk score as an internet-facing gateway (Home), even if they share the same software flaw.
The solution: Automate the environment (as much as humanly possible)
While the academic argument is sound, it is impossible for a human team to manually calculate Environmental scores for every asset in a sprawling network. vRx xTags are designed to solve this by automating the "Hospital vs. Home" math, helping you to identify and prioritize the parameters that profile assets. With tags such as "External," "PCI-DSS," or "Sandbox," the vRx engine automatically adjusts the risk score, instantly downgrading the noise so you can focus on the true Criticals.
The following diagram is an overlay of the study’s BTE framework onto vRx’s dashboard to illustrate how the “Base Score + Threat Intel + Context (xTags)” formula can help to classify and prioritize large numbers of vulnerabilities to highlight those few that matter most urgently:
Reality check: Threat intelligence really does cut the noise
The study highlights a critical flaw in the standard scoring model. The default assumption for the "Threat" metric is "Active Exploitation," meaning that unless you intervene, the system assumes hackers are currently actively using every vulnerability in your backlog with the same amount of zeal. When the researchers checked real threat data, however, the majority of vulnerabilities fell into "Class U" (Unreported), meaning there was no evidence of exploitation or even proof-of-concept code in the wild. Of course, we live in a world where agentic AI can use LLMs to vibe-code exploits straight from a reading of the CVSS posting itself; while that statistic might not mean what it used to, such AI use also supports the paper’s thesis that we are (and will, let’s face it, increasingly be) in need of better ways to filter out the noise and that we can clearly no longer trust our old assumptions about threat management,
Prioritization requires threat data
Adding threat metrics significantly changes vulnerability prioritization by suppressing the scores of bugs that hackers aren't actually using. The research underscores that there is often zero correlation between a high Base Score and actual exploitation in the wild. Lacking sufficient insight into exploit maturity, security teams are essentially forced to treat theoretical risks with the same urgency as active attacks. At best, this is an inefficient use of limited resources; at worst, an active distraction from imminent attacks or ongoing breaches.
The vRx proposition: Don't hunt ghosts
This is where the vRx threat engine becomes essential. By ingesting the same data sources cited in the paper, such as the CISA Known Exploited Vulnerabilities (KEV) catalog and various exploit databases, it automates the Threat component of the score in an in-depth and multifaceted way. If a CVE has a terrifying 9.0 rating but no active exploit exists, vRx might note it but deprioritize it. Conversely, if a lower-rated bug is wormable and actively spreading, the system flags it, ensuring you are fighting real fires rather than chasing smoke.
From scoring to solving
The paper concludes that utilizing the full BTE (Base, Threat, Environment) scoring model makes risk representation "more accurate and more actionable." No matter how accurate, though, a score is ultimately just a number; the milieu and other technicalities are what turn it into a multidimensional problem. The academic approach identifies the problem and calculates the risk, but it stops short of factoring in the solution. vRx takes the "Actionable Score" and attaches it to a suggested automated action. While the research suggests you should calculate the score to understand the risk, vRx enables you to calculate the real risk score and immediately either deploy the patch or apply Patchless Protection. Because the platform automates both the context and the threat data, it can safely automate the remediation and thereby close the loop between scientific assessment and practical security.
Transforming Risk Management into Risk Elimination
The era of trying to fix every vulnerability is over; the math simply does not work. This scientific research confirms that relying on "context-blind" Base Scores forces organizations to waste time on nearly 40% of their backlog. Sticking to spreadsheets and manual calculations isn't just inefficient anymore; it has demonstrably become too slow, scientifically inaccurate, and mathematically unsustainable to compare. By adopting a context-aware approach, you can filter out the alarmism and focus on the risks that truly threaten your business.
Stop managing a list of possibly-maybe-inflated scores and start eliminating actual evidence-based risk. You could manually try to replicate this complex research, or you can leverage a platform built on turning these exact principles into a defense-in-depth posture. Book a demo today to see how vRx turns science into strategy!





%20Signals%20a%20New%20Era%20of%20Supply%20Chain%20Risk.png)








