
Software development has seen some fundamental transformation with the "Shift Left" security paradigm, which pushes responsibility for security earlier in the lifecycle. This has, arguably, introduced a significant blind spot; by concentrating security tools and permissions on their developer workstations, organizations have inadvertently turned these environments into high-value targets for adversaries seeking to bypass hardened production perimeters. These machines are often rich with SSH keys, cloud credentials, and source code, yet they frequently lack the rigorous monitoring applied to production servers. This disparity has made Integrated Development Environments (IDEs) a primary vector for modern supply-chain attacks. In this landscape, VS Code’s visibility and prominence have made it an ideal target; its attendant rapid user base growth and relatively recent open-sourcing translate into a large and relatively inexperienced cohort for cyber-criminals to exploit.
The threat landscape: Why developers are the new targets
The core of this emerging threat lies in the "Trust Gap" inherent to extension marketplaces. Despite marketplaces offering a veneer of security through "Verified Publisher" badges, these often only verify domain ownership rather than the safety or integrity of the code itself, leading developers to implicitly trust malicious tools. The "TigerJack" campaign serves as a stark illustration of this vulnerability, where over 17,000 downloads of fake tools occurred because developers assumed marketplace presence equaled security vetting.
The year 2025 has seen a rapid escalation of this threat vector. Data indicates a quadrupling of malicious extension detections, marking a distinct shift from simple nuisanceware to sophisticated espionage tools capable of deep infiltration. This trend highlights that threat actors are now specifically targeting developer environments as a strategic entry point into the broader organization. Unlike mobile applications or web browsers, VS Code extensions present a systemic risk because they operate without a sandbox and often inherit the full privileges of the developer user, meaning any malicious code within an extension has root-level access to the host system.
Common attack vectors and techniques
Attackers employ a variety of deceptive tactics to infiltrate developer environments, moving beyond simple malware drops to sophisticated social engineering and supply chain manipulation. These techniques often exploit the developer's need for speed and efficiency, embedding threats in tools that appear necessary or helpful for daily tasks.
Typosquatting and brandjacking
This remains one of the most prevalent methods, where adversaries mimic popular tools to trick hurried developers; a notable example is the "Icon Theme: Material" attack, which cloned a popular legitimate extension to deploy Rust-based malware. These attacks rely heavily on visual similarity (i.e. copying icons, descriptions, copywriting styles, and brand nomenclatures) to bypass developer scrutiny and secure an install base before the community flags the deception.
Trojanized functionality
A more insidious method involves creating extensions that perform a genuine, useful task to mask background malicious activity. Extensions like Codo AI and Bitcoin Black successfully delivered real features, such as code formatting or AI assistance, while simultaneously stealing session cookies in the background. This dual nature makes detection exceptionally difficult, as the tool functions exactly as intended, giving the user no immediate reason to suspect foul play.
Dependency poisoning
Attackers are also increasingly hiding malware deep inside node_modules dependencies rather than the primary extension files. A recent campaign involving the path-is-absolute npm package demonstrated this by concealing malicious binaries inside a fake PNG file. By burying the threat within the complex tree of dependencies, attackers ensure that standard code reviews of the main extension often fail to uncover the malicious payload.
Living off the land (LOLBins)
Sophisticated attackers are using legitimate system binaries to evade standard antivirus detection. By abusing tools like cmstp.exe or Lightshot to execute payloads, malicious extensions avoid dropping known malware files directly to disk. This "fileless" approach renders traditional file-based scanning less effective, as the malicious activity is carried out by trusted system processes.
Exfiltration and persistence strategies
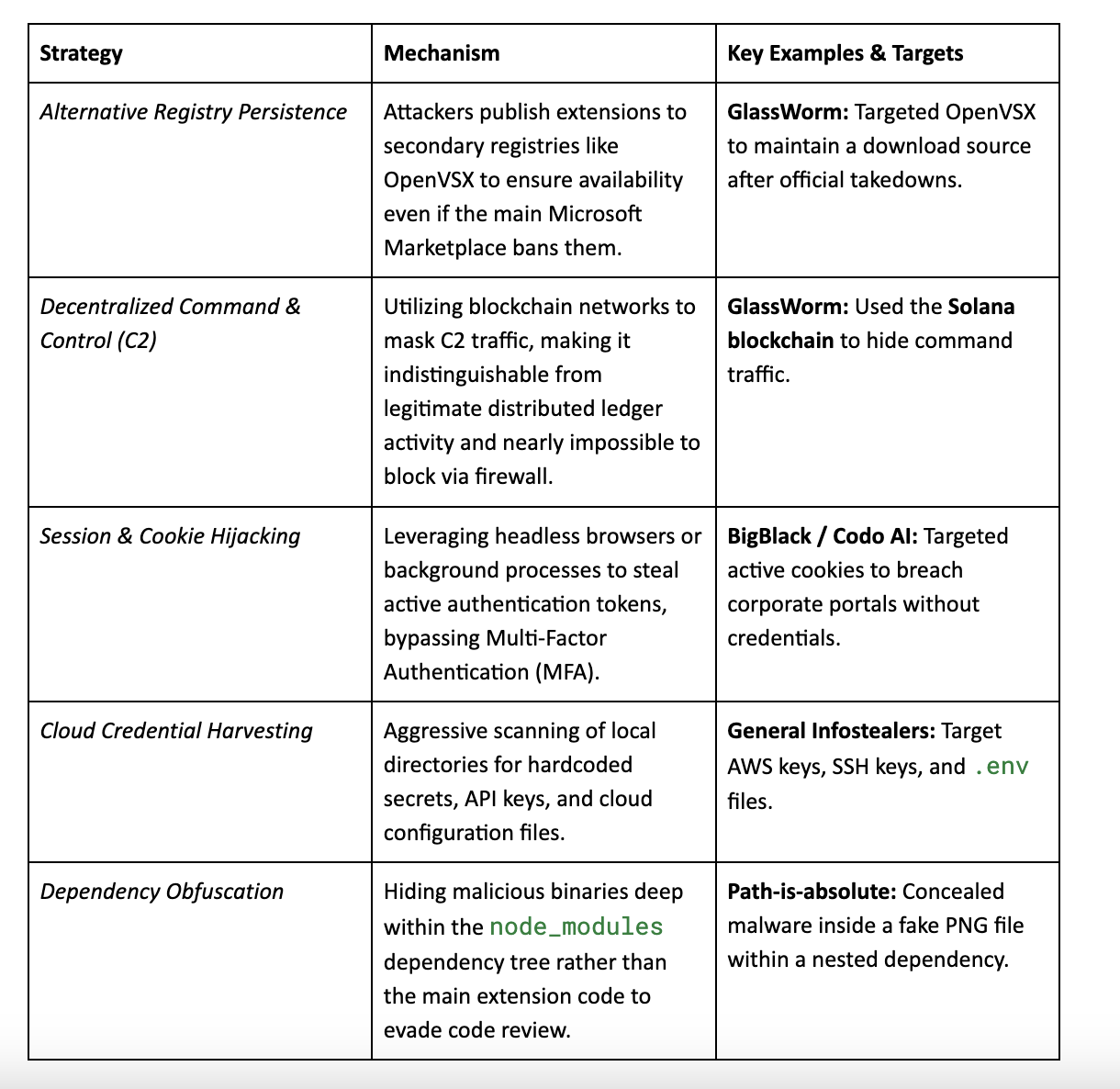
Modern malicious extensions are engineered for longevity, designed to maintain access long after the initial compromise or the closure of the IDE. Rather than simple smash-and-grab operations, these tools employ sophisticated evasion techniques to bypass firewalls and establish long-term footholds within the developer's environment.
The following are some strategies attackers use to ensure persistence and exfiltrate sensitive data:

Detection and destruction
Effective detection requires a multi-layered approach that combines manual vigilance with automated fleet management. Security teams must recognize that standard endpoint protection often overlooks the nuances of IDE-specific threats.
Manual hunting in directories
Proactive "hunting" in the ~/.vscode/extensions directory is a necessary defense layer. Visual red flags can often reveal compromised extensions that automated tools might miss. Look for obfuscated code within extension.js, unusual file types like .vbs or .bat that have no place in a standard extension, or mismatched publisher names that do not align with the official vendor.
Scalable fleet detection
Scalable detection requires leveraging tools like Osquery. By querying the vscode_extensions table, administrators can scan an entire fleet for specific dangerous publisher IDs or identify any extensions installed within the last 24 hours. This capability allows for rapid assessment of widespread exposure across the organization, transforming a manual check into a queryable dataset.
Network behavior monitoring
Network-based detection methods are critical for catching active breaches. Security teams should monitor for suspicious "phone home" behaviors immediately upon VS Code launch. Indicators of compromise include immediate connections to dynamic DNS services or non-Microsoft IP addresses, which often signal an extension attempting to establish a C2 channel or exfiltrate environment variables.
Prevention and governance
Mitigating the risk of malicious extensions requires shifting from a reactive stance to a governance-first model. Organizations must implement controls that limit what code can run in the developer environment without hindering productivity.
Enterprise allowlisting
Enterprise environments should implement a strict "Allowlist" approach. Using Group Policy or settings.json, organizations can block all extensions by default and only permit a vetted list of Publisher IDs, such as restricting installs solely to "Microsoft" and "GitHub". This drastically reduces the attack surface by eliminating the possibility of developers installing unverified third-party tools, forcing a review process for new additions.
Leveraging workspace trust
VS Code Workspace Trust plays a vital role in preventing "drive-by" attacks. While utilizing "Restricted Mode" can mitigate risks when opening untrusted repositories, it is important to clarify that this feature does not fully neutralize extensions that are already installed globally. It serves as a containment measure for new code sources, but is not a cure for a previously compromised environment.
Limiting blast radius
Organizations must limit the "blast radius" of a potential compromise. Best practices include using short-lived credentials through key rotation and implementing secret scanning tools. These measures ensure that if a developer machine is compromised, the stolen keys are likely invalid or quickly revoked, minimizing the potential damage and preventing lateral movement into production. The use of virtualization techniques like containerization on developer machines can also help to mitigate the potential scope of breaches on developer machines.

From detection to remediation, automatically
When prevention fails, rapid remediation is essential. vRx by Vicarius is a vulnerability remediation platform purpose-built to address the most critical part of the vulnerability lifecycle: fixing the problem. While many tools focus heavily on detection, vRx prioritizes the mobilization and remediation of exposures, allowing organizations to move quickly from identification to resolution. This approach is particularly effective for managing vulnerabilities that lack standard CVEs, such as malicious software components or configuration flaws found in developer tools.
Key capabilities for securing the developer supply chain include:
- Scripting engine for surgical remediation: Security teams can leverage the proprietary, automation-first technology in vRx to deploy scripts that terminate the VS Code process and delete specific malicious extension directories across thousands of endpoints simultaneously.
- Patchless protection: vRx provides in-memory protection for underlying developer tools, such as Node.js or Python runtimes, offering a defense layer when official vendor patches are not yet available.
- Native Patching: vRx delivers native, end-to-end patching built directly into the platform, eliminating the need for tickets, handoffs, or external tools. It supports automated patching for operating systems and over 10,000 third-party applications from a single control plane, using pre-tested remediation packages, flexible deployment policies, and safe rollout mechanisms such as scheduling, maintenance windows, and rollback. Instead of documenting risk or waiting on manual intervention, vRx closes the loop by turning detected exposures into verified fixes at scale.sa
A surgical response for supply chain security
The security challenges facing modern development environments are deeply rooted in the open-source ecosystem, yet the solution also lies in leveraging the best of this community. While the "Shift Left" movement and the open nature of VS Code have created new avenues for supply chain attacks, they have also fostered the innovation necessary to defend against them. vRx embodies this duality through its "Better Together" initiative, which enables seamless integration with the existing scanners and security tools organizations already rely on. By connecting detection with automated remediation, vRx closes the loop, taking alerts from scanners and turning them into practical fixes. Are you ready to secure your developer environments? Book a demo session today to discover the vRx difference.







%20Signals%20a%20New%20Era%20of%20Supply%20Chain%20Risk.png)






