
Security teams are swamped by alerts, sprawling hybrid estates, and an endless stream of CVEs. The answer isn’t “more scans”. It’s exposure management, a continuous, business-aligned program that aims for measurable exposure reduction and sustained attack surface reduction. Gartner’s model for this shift is Continuous Threat Exposure Management (CTEM): a five-stage, repeatable cycle designed to keep attention on what truly threatens the business.
What is Exposure Management and what makes CTEM different?
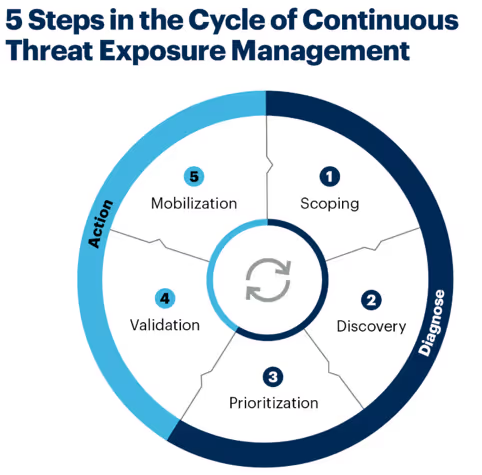
Exposure management looks beyond vulnerability lists to include misconfigurations, risky identities/permissions, SaaS drift, and the attack paths that actually connect entry points to crown-jewel assets. CTEM operationalizes that approach as a continuous loop of scoping, discovery, prioritization, validation, and mobilization. Gartner lays out the five steps here: How to Manage Cybersecurity Threats, Not Episodes. For an accessible summary, Splunk’s explainer on CTEM covers the same five stages and highlights the move from periodic to continuous defense.
Why CTEM now: separate the signal from the noise
The core problem is signal-to-noise. Cisco/Kenna’s research shows only ~5% of vulnerabilities are likely to be exploited; most issues never become weaponized, which means fix-everything lists waste precious cycles (Cisco newsroom). CTEM directs effort to the small subset that matters driving exposure reduction where it reduces real risk.
Attackers also tend to reach critical assets through a few converging routes. CSO Online reported that adversaries can compromise 94% of critical assets within four steps of an initial breach, emphasizing the importance of mapping and mitigating attack paths (CSO Online). In parallel, CPO Magazine summarized that a tiny fraction of exposures create most of the real danger, a powerful case for CTEM’s focus on choke points and attack surface reduction (CPO Magazine).
Finally, even the “obvious” lists aren’t equal. SecurityWeek recently noted that items in CISA’s KEV catalog vary in impact depending on environment and context, reinforcing the need for prioritization over raw severity (SecurityWeek).
The CTEM five-stage program
1) Scoping - Decide what truly matters: crown-jewel apps, high-value data stores, internet-facing services, identity tier-0, and critical SaaS. Good scoping keeps exposure management efforts focused on business outcomes and sets a baseline for attack surface reduction. Gartner’s piece walks through how to scope systematically (Gartner).
2) Discovery - Move beyond CVEs. Map misconfigurations across cloud/IaC, excess permissions in IAM, unmanaged SaaS, and external exposure. Splunk’s CTEM primer covers the importance of continuous discovery across the entire estate (Splunk). Continuous discovery is where exposure management starts producing actionable exposure reduction.
3) Prioritization - Not every finding is equal. Use exploit likelihood (e.g., EPSS), environmental context, asset criticality, and path analysis to rank what to fix. Cisco/Kenna’s data-driven view fix the fraction most likely to be exploited maps directly to continuous threat exposure management (CTEM) and meaningful attack surface reduction (Cisco newsroom).
4) Validation - Validation should prove an exposure truly matters. Many organizations rely on BAS platforms, purple-team exercises, or pen tests to simulate attacker behavior and confirm exploitability. While these methods can provide insight, they are often slow, resource-heavy, and limited to narrow subsets of systems. Because of that, they don’t scale effectively across the entire enterprise, leaving large portions of the environment unvalidated and making continuous validation difficult to sustain.
5) Mobilization - Turn decisions into action: patches, config changes, segmentation, identity right-sizing, and compensating controls executed with clear ownership and SLAs. Gartner stresses moving from episodic fixes to continuous, cross-functional execution as the heart of continuous threat exposure management (CTEM) (Gartner).
Proof points leaders can share with the board
- Breach-likelihood reduction: Gartner projects that organizations prioritizing investments through CTEM will be 3× less likely to suffer a breach by 2026. That’s a direct, business-level justification for exposure management.
- Focus on the 5%: Cisco/Kenna’s findings show only a small subset is likely to be exploited so target exposure reduction there.
- Attack paths matter: Media analyses emphasize how a few paths account for most risk, illustrating why attack surface reduction should eliminate chokepoints rather than chase every low-impact issue.
Implementing CTEM: a practical playbook
- Secure executive sponsorship by framing exposure management in risk and resilience terms breach-likelihood reduction, audit readiness, and cost avoidance. Forbes makes the case that automation-first approaches are now table stakes for keeping pace (Forbes).
- Scope your attack surface (crown jewels, internet-facing, identity tier-0, SaaS). Tie scope to regulatory or revenue-impacting processes to drive attack surface reduction where it matters most. (Gartner).
- Deploy continuous discovery for vulnerabilities, misconfigurations, and identity drift across cloud, data center, and SaaS.
- Prioritize with context using exploit likelihood and business criticality. Cisco’s analysis shows why this approach outperforms severity-only triage.
- Validate before you mobilize. Confirm which exposures are truly exploitable and could impact critical assets. Without this step, teams risk pouring effort into issues that don’t reduce risk, making exposure reduction less effective.
- Mobilize with automation and SLAs patch when safe, reconfigure when faster, add controls when patching isn’t possible. SecurityWeek’s caution on treating “critical lists” with context supports this disciplined mobilization (SecurityWeek).
- Measure outcomes: report exposure reduction, median time-to-remediate validated items, and year-over-year attack surface reduction to show progress.
Vicarius’s approach to CTEM
At Vicarius we design exposure management to be continuous, validated, and outcome-driven:
- Scoping: map and weight assets by business impact.
- Discovery: extend beyond CVEs to misconfigurations, application exposures, and external attack surface.
- Prioritization: rank by exploitability, business impact, and environmental context.
- Validation: Vicarius doesn’t rely on Breach-and-Attack Simulation (BAS), which is often slow, resource-intensive, and limited to small subsets of systems. Instead, we validate exposures by calculating the probability of exploitability using threat intelligence, exploit availability, and environmental context, so teams focus only on exposures most likely to be weaponized.
- Mobilization: orchestrate fixes and compensating controls to achieve durable exposure reduction and measurable attack surface reduction.
This is continuous threat exposure management (CTEM) in practice turning signals into action, and action into sustained resilience.
%20to%20Reduce%20Attack%20Surface.avif)











