
Traditional vulnerability management was built for periodic scans and patch cycles, yet attackers now weaponize exploits within days and regulators demand incident reporting within hours. In this environment, executives and security leaders are embracing Preemptive Exposure Management (PEM) and its codified implementation, Continuous Threat Exposure Management (CTEM), to reduce attack surfaces and build resilience before breaches occur. Gartner predicts that by 2026 organizations prioritizing investments in CTEM will be three times less likely to suffer a breach, while other research shows CTEM programs can yield ten-times better asset visibility and 82% fewer remediation tickets.
This article explores the latest innovations, frameworks and sector-specific drivers shaping this movement and offers a roadmap for operationalizing PEM.
Understanding Preemptive Exposure Management
Preemptive exposure management goes beyond simply detecting and responding to threats. Vicarius defines PEM as a strategy that continuously discovers assets, uses artificial intelligence (AI) to prioritize exposures, automatically remediates risk, and delivers unified dashboards for visibility across the attack surface. Instead of waiting for vulnerabilities to be exploited, PEM proactively eliminates opportunities for attackers. Morphisec notes that a preemptive approach aims to remove exposures before adversaries can exploit them, contrasting with proactive security that merely anticipates attacks. PEM integrates AI-powered risk validation, policy-based remediation and automated processes, enabling security teams to reduce mean time to remediate (MTTR) and align with the organization’s risk appetite. It is intimately linked to CTEM, which provides the structured program to manage exposures continuously.
CTEM: From Buzzword to Blueprint
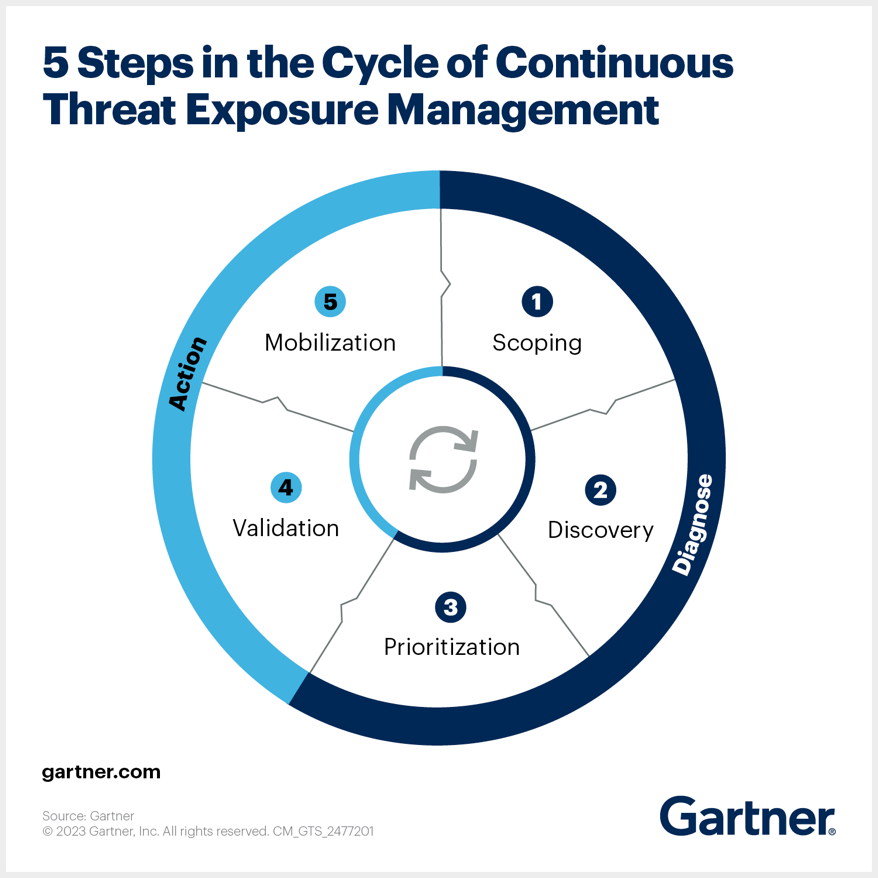
Gartner’s Continuous Threat Exposure Management is a five-phase program: scoping, discovery, prioritization, validation and mobilization that runs on a continuous loop. Recorded Future’s CISO guide explains that CTEM goes beyond traditional vulnerability management by continuously discovering assets, assessing risk based on business impact, validating exploitable attack paths and orchestrating remediation.
A key distinction from legacy vulnerability management is that CTEM prioritizes exposures by their potential to compromise “crown-jewel” assets rather than raw CVSS scores. This shift is vital because research shows that only about 5% of vulnerabilities are likely to be exploited and the 2025 State of Threat Exposure Management report found that just 0.002% (1 in 50,000) of vulnerabilities pose critical risk. By filtering out the noise and focusing on what attackers can actually leverage, such as the 1 in 20 vulnerabilities actively exploited in the wild and the 1 in 100 that are internet-facing, CTEM helps teams allocate limited resources effectively.
Innovations Driving PEM and CTEM
Recent innovations are making preemptive exposure management more practical and powerful:
- AI-driven exposure discovery and prediction – Armis notes that the number of connected assets will surpass 50 billion by 2025, most of which are unseen or unmanaged. Generative AI can analyze vast data to identify vulnerabilities, anticipate potential risk and continuously learn from new threat patterns. AI systems enhance visibility by unifying asset inventories, profiling devices, providing contextual intelligence and even reverse engineering malware for early warning.
- Attack surface management (ASM) – With organizations deploying hundreds of digital services every month, external attack surfaces expand rapidly. SentinelOne explains that ASM continuously identifies, assesses and monitors digital assets, including shadow IT, to provide up-to-date views of the environment. Benefits include real-time detection of changes, automated discovery of unknown assets, risk prioritization, compliance support and proactive mitigation. ASM tools form the discovery layer for CTEM and feed AI systems with live data.
- Virtual analysts and AI-driven remediation – At RSA Conference 2025, vendors showcased AI “virtual analysts” that recommend and even execute remediation actions, bridging the gap between detection and response. Integrations between purple team operations (offensive and defensive collaboration), data-layer exposure management, and identity-centric risk scanning were highlighted, underscoring the expansion of CTEM beyond infrastructure to data and identity. These innovations shorten the cycle between discovery and mitigation, enabling preemptive defense.
- Continuous identity and data exposure scanning – Attackers often exploit misconfigurations in identity and access systems. New CTEM tools assess directory settings, over-privileged accounts and misconfigured cloud storage, closing backdoors before they are abused.
- Generative AI for exposure management – By learning from adversary tactics, generative models can perform early-stage reconnaissance and emulate attacker behavior to identify exposures earlier than traditional scans. In addition, generative AI can now normalize and deduplicate exposure data, prioritize remediation and provide targeted guidance.
- DevSecOps integration – For technology companies, preemptive exposure management is intertwined with DevSecOps. DevSecOps embeds security into every stage of the software development lifecycle, emphasizing shift-left practices, automation and continuous monitoring. Automated security tests run within CI/CD pipelines so vulnerabilities are flagged and remediated in near real time. This integration reduces technical debt and ensures code is secure before deployment.

Sector-Specific Drivers and Use Cases
Finance: Regulatory Pressure and Preemptive Compliance
Financial institutions operate under strict scrutiny. Morphisec explains that regulators such as the New York Department of Financial Services (NYDFS), the Securities and Exchange Commission (SEC) and federal banking agencies have tightened cybersecurity rules, signaling that reactive security models are no longer enough. Updated NYDFS regulations phasing in through 2025 require annual certifications, mandatory vulnerability scanning, multi-factor authentication and enhanced governance, with boards overseeing cyber programs. Agencies also mandate that banks notify regulators of material incidents within 36 hours and enforce cybersecurity standards across third parties.
These mandates drive adoption of preemptive exposure management. Institutions must continuously monitor, conduct proactive risk assessments and maintain readiness to meet compressed reporting timelines. In practice, this means deploying CTEM programs that map critical financial systems, prioritize exposures based on regulatory risk, and validate controls through attack simulations.
An Obviam case study reports that a mid-sized financial services firm implemented daily automated discovery, weekly validation and monthly simulations, leading to a reduction in mean time to remediate and zero security incidents. Preemptive models also help financial institutions avoid unnecessary disclosures when attacks are neutralized early, incidents never become material, easing compliance burdens. Vendors like Morphisec provide moving target defense and adaptive exposure management to neutralize threats before they take hold, meeting regulators’ expectations for proactive controls.
Healthcare: Managing IoMT and Critical Systems
Healthcare organizations face unique exposures from medical devices (IoMT) and operational technology (OT). A Claroty study analyzing over 2.25 million IoMT devices and 647,000 OT devices across 351 healthcare providers found that 89% of organizations run medical systems vulnerable to known exploited vulnerabilities (KEVs) and 99% have systems with publicly exploited vulnerabilities. Imaging systems and hospital information systems are particularly exposed; roughly 20% of hospital information systems carry KEVs and are insecurely connected to the internet. This fragility has real consequences: 78% of surveyed organizations reported ransom payments of $500k or more after cyber incidents.
Preemptive exposure management helps healthcare providers protect patient safety and reduce costly disruptions. The Obviam case study shows a healthcare provider implementing CTEM to monitor patient-facing systems, prioritize exposures based on patient safety, validate high-risk exposures through simulated attacks and reduce externally exposed services and critical vulnerability age. CTEM allows organizations to continuously inventory devices, correlate vulnerabilities with patient care impacts and orchestrate rapid remediation, all while navigating stringent privacy regulations.
Technology: DevSecOps and Attack Surface Velocity
Technology companies deploy code and infrastructure at breakneck speed. Traditional periodic scanning cannot keep pace with agile release cycles. DevSecOps practices integrate security into development pipelines; key principles include shift-left security, automation, collaboration and continuous monitoring. Automation runs static and dynamic analysis, compliance checks and vulnerability assessments at every stage of the CI/CD pipeline, providing immediate feedback and preventing insecure code from progressing. Continuous monitoring tools observe applications and infrastructure for misconfigurations and anomalies in real time. By embedding CTEM into DevSecOps, technology firms achieve rapid detection and preemptive remediation without sacrificing agility.
At RSA 2025, CTEM innovations tailored to tech were on display. Vendors showcased AI-powered “virtual analysts” that interpret exposure data and recommend remediation actions, purple team integrations that unify offensive and defensive teams, and identity-centric risk scanning to discover misconfigured permissions. Such tools empower lean security teams to manage complex multi-cloud environments. A 3rd party vendor report reinforces the scale of the challenge: even with millions of scanned assets, only 1 in 50,000 vulnerabilities is critical , yet 39% of organizations miss service level agreement (SLA) targets for top-priority patching due to volume and fragmentation. To close these gaps, 95% of organizations plan to adopt new vulnerability or exposure management platforms that combine real-time insights with automation. This trend emphasizes the necessity of AI-enhanced CTEM solutions for the tech sector.
Government: Constant Authorization and Mission Assurance
Government agencies manage mission-critical systems that cannot afford downtime. Recognizing the limitations of static risk frameworks, the U.S. Department of Defense (DoD) replaced its Risk Management Framework with the Cybersecurity Risk Management Construct (CSRMC) in September 2025. According to Akin Gump’s analysis, the CSRMC emphasizes automation, continuous monitoring and reciprocity, moving away from checklist-driven processes. It aims to embed cybersecurity throughout the system lifecycle, providing real-time dashboards and automated alerts that enable a “constant Authority to Operate (ATO)” posture rather than periodic reviews.
The framework is grounded in ten principles, including automation, focus on critical controls, continuous monitoring, DevSecOps integration, cyber survivability, training, enterprise services and inheritance, operationalization, reciprocity and threat-informed assessments. Building on these tenets, the CSRMC organizes cybersecurity into five phases: design (embedding resilience into architecture), build (integrating security into development), test (conducting threat-informed validation), onboard (initiating continuous monitoring for constant ATO) and operations (maintaining real-time dashboards and the authority to disconnect systems that exceed risk tolerances). This government example shows how preemptive exposure management underpins national defense and provides a model for other sectors.
Best Practices and Caveats for Operationalizing PEM
Successfully implementing preemptive exposure management requires more than purchasing tools. The following recommendations synthesize expert guidance and case study lessons:
- Define crown-jewel assets and business context (Scoping) – Identify the systems, data and processes that are most critical to mission or revenue. Understanding business impact guides prioritization and ensures security investments align with risk appetite.
- Continuously discover and inventory assets – Use discovery and asset intelligence tools to map all endpoints, cloud services, IoT/OT devices and shadow IT. Unified inventories reduce blind spots and provide the foundation for exposure analysis.
- Prioritize based on exploitability and impact – Apply contextual risk scoring that considers active threat campaigns, internet exposure, existing defenses and proximity to critical assets. Focus on the small fraction of vulnerabilities that are truly exploitable.
- Validate through threat simulation – Red and purple team exercises, while invaluable, are manual, episodic, and resource-intensive. Each simulation requires specialized expertise, tooling, and coordination across teams. As organizations face thousands of new exposures daily, validating each through a live test becomes impractical and costly. Moreover, these exercises often provide only a snapshot in time, missing the continuous evolution of threats, configurations, and patch states. The result is partial assurance rather than ongoing validation.
- Automate remediation and mobilization – Use orchestration and playbooks to resolve exposures at scale. AI-driven virtual analysts can recommend patches, configuration changes or compensating controls and trigger them automatically, reducing MTTR. Establish service-level agreements for remediation and measure outcomes to drive accountability.
- Integrate with DevSecOps and operations – Embed CTEM processes into CI/CD pipelines, infrastructure-as-code and operational workflows. Automated security testing, continuous monitoring and policy enforcement should run alongside development and operations tasks. This integration ensures that exposures are addressed before deployment.
- Embrace AI responsibly – Leverage generative AI for early exposure detection, anomaly detection and contextual analysis, but maintain human oversight. Ensure AI models are trained on diverse datasets and incorporate explainability to avoid bias.
- Foster cross-functional collaboration and reporting – Preemptive exposure management is not solely an IT function. Engage risk management, compliance, operations and executive leadership in program design and reporting. Provide clear metrics such as reduction in attack surface, MTTR, and validation results to communicate progress and justify investments.
A Call to Action for Cyber and Risk Leaders
The cyber landscape of 2025–2026 demands a paradigm shift. Attack surfaces are exploding, vulnerabilities are weaponized faster than ever, and regulators expect rapid reporting and demonstrable resilience. Traditional reactive defenses cannot keep up. Preemptive exposure management, operationalized through continuous threat exposure management, offers a compelling path forward. By unifying continuous discovery, AI-driven prioritization, threat-informed validation and automated remediation, organizations can reduce risk faster, optimize resources and align security with business objectives.
The evidence is clear: only a tiny fraction of vulnerabilities are truly critical , yet legacy processes drown teams in noise and missed SLAs. Sectors as varied as finance, healthcare, technology and government are already moving toward preemptive models, driven by regulatory mandates , patient safety concerns , software velocity and mission assurance. Early adopters are reaping benefits: reduced incident rates, faster remediation and improved resilience.
Cybersecurity and risk leaders cannot afford complacency. Embracing PEM requires commitment investing in AI-enabled tools, redesigning processes around CTEM, cultivating a culture of continuous improvement and collaborating across the enterprise. But the payoff is profound: fewer breaches, stronger regulatory compliance, enhanced trust and the freedom to innovate securely. The time to act is now. Make preemptive exposure management a strategic imperative and position your organization to thrive in the face of relentless cyber threats.














