Katie: Welcome back to the Deep Dive. We're here to cut through the noise and give you the insights you need and do it fast.
James: Glad to be here.
Katie: So today we're tackling something that's just, well, it's escalating incredibly quickly. Cyber threats.
James: Absolutely. The pace is relentless.
Katie: It really feels like this constant race, doesn't it? A new vulnerability pops up and almost immediately, I mean, before most places can even blink, it's being used by attackers.
James: That's exactly right. And security teams, they're just grappling with this massive, complex attack surface. It's not just growing, it's exploding.
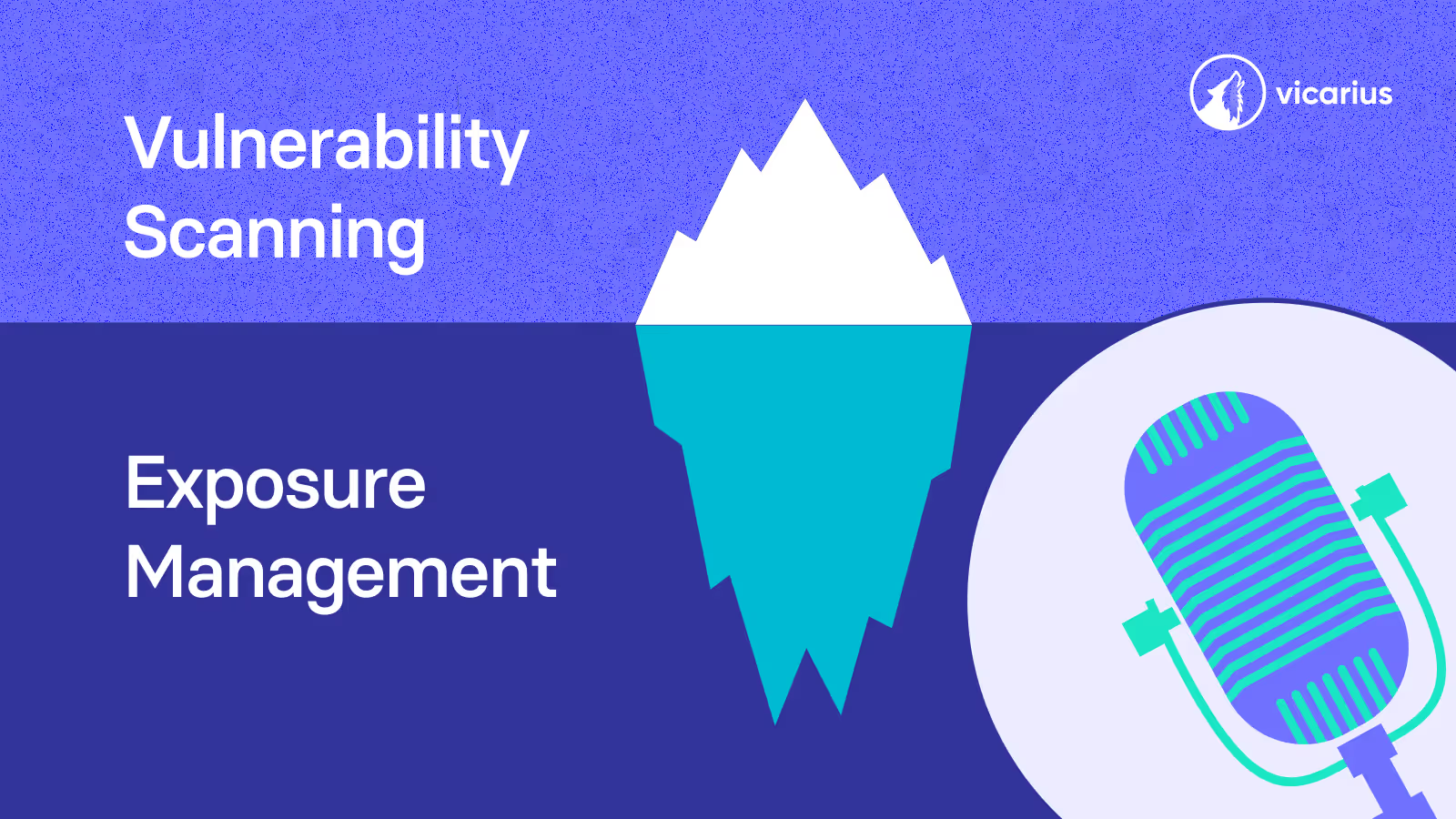
Katie: Yeah, exploding is the right word. And it really makes you step back and think, in this world so connected, so vulnerable, is just finding the problems really enough anymore.
James: That's the million-dollar question, isn't it?
Katie: Or do we need a totally new approach, something to actually fix things and fix them fast and effectively?
James: A more proactive stance, essentially.
Katie: Precisely. And that question is really at the heart of our deep dive today. We're going to unpack something called an exposure management platform, an EMP.
James: Right, EMP.
Katie: Think of it like a modern cybersecurity solution. It doesn't just, you know, scan for weak spots. It actively manages and really works to reduce the chance of those weaknesses being exploited across everything you own digitally.
James: It's a fundamental shift from just visibility to actual risk reduction.
Katie: Our mission here today is to give you, our listener, a really clear, actionable grasp of what an EMP actually is. How it's fundamentally different from, say, older vulnerability management tools.
James: Which many are still using.
Katie: Exactly. And why it's becoming, well, almost non-negotiable for modern security, plus the real tangible benefits you get.
James: We're hoping for a few aha moments today.
Katie: Yeah, hopefully moments that might just shift how you think about tackling cybersecurity challenges.
James: Good goal.
Katie: So to really get this, we'll start with the basics. What is an EMP? Then we'll contrast it with those older ways.
James: The classic VEM approach.
Katie: Right. Then we'll look at the big forces driving this change, forces probably hitting your security posture right now.
James: I know.
Katie: Then we'll break down how these platforms actually work, that continuous loop idea. And finally, what really matters if you're considering one, key features.
James: Sounds like a plan.
Katie: Okay, let's dive right in. When we talk about an exposure management platform, what exactly are we defining? What's the core idea?
James: Well, it's interesting because an EMP isn't just, you know, another tool in the toolbox. It really represents a strategic change. Okay. Our sources define it as a cybersecurity solution built to continuously identify all your digital assets, everything.
Katie: Continuously. That sounds key.
James: It is. Then it analyzes their exposure risk, but crucially within your specific business context.
Katie: So not just technical severity.
James: Exactly. It understands what matters to the business. And then the really critical part, it automates remediation workflows.
Katie: Oh, the action part.
James: Yes. To dramatically cut down the likelihood of exploitation across your whole attack surface. It's about moving past that fragmented approach. You know, multiple tools, manual sorting.
Katie: And the spreadsheets.
James: Right. Towards a unified system. Discovery, smart prioritization, and rapid response. It's delivering what the industry calls continuous threat exposure management at scale. CTEM, basically.
Katie: That sounds incredibly comprehensive. Yeah. So how does that stack up against or differ from traditional vulnerability management, VM, the thing most people are familiar with?
James: Yeah. And it's a really, really critical distinction to make. Traditional VM tools, their main job is finding and listing known CVEs, common vulnerabilities and exposures.
Katie: Your list generators.
James: Pretty much. They give you a severity score, often CVSS, the common vulnerability scoring system score, which is a standardized baseline. OK. But here's the main difference. VM largely leads the action part, the remediation planning, the fixing. Totally up to you, the user. You get this long list.
Katie: And good luck.
James: Basically, yeah. You figure out what to do next. An exposure management platform, though, takes a much more active role. It goes way further. It pulls in real-time threat intelligence.
Katie: So what attackers are actually doing now?
James: Exactly. It understands the full business context of every asset. How critical is it? Who use it? What data is on it? And it builds automated remediation logic right into the platform. So the whole question shifts from just what's broken to something much more useful.
Katie: Which is?
James: Which is, what's truly at risk right now? And what can we fix immediately to protect our most vital assets? It's proactive and business focused.
Katie: That's a huge difference. Can you maybe paint a picture like a real-world example where this difference really hits home?
James: Sure, absolutely. Let's take a common scenario. A new CVE drops for a really popular PDF viewer. Everyone uses it.
Katie: OK, happens all the time.
James: Right. So a traditional VM tool, it scans, and boom, it flags every single copy of that PDF viewer. Hundreds, maybe thousands of endpoints across your company. Oh, wow. And it treats them all the same. You're left staring at this massive, kind of terrifying list of potential problems.
Katie: Yeah, alert fatigue central.
James: Totally. Now contrast that with an EMP. It works smarter. It knows which of those machines are facing the internet.
Katie: Higher risk there.
James: Definitely. It knows which users on those machines have admin rights, privilege access. And it might even know which systems, okay, they're unpatched, but they're protected by something like application sandboxing.
Katie: So mitigating controls are factored in.
James: Precisely. So instead of that giant noisy list, the EMP flags only the subset that's truly exploitable and high risk for immediate action.
Katie: Ah, focus.
James: Exactly. It saves the security team a huge amount of time, cuts down that alert fatigue massively, and lets them focus their precious resources where it counts most. It's precision over sheer volume.
Katie: That makes perfect sense.
James: So yeah, quick contrast. VM is about finding known CVEs, scanning periodically, giving lists EMP. It's about understanding real exposure, continuous monitoring, and driving actionable, often automated fixes aligned with modern security needs like CTEM.
Katie: That PDF example really clarifies why just scanning isn't cutting it. It feels like this EMP approach isn't just a nice to have anymore. It's becoming essential. But why the urgency? Why now? What are the big pressures making this shift so critical today?
James: That really is the crux of it, isn't it? And there are, I'd say, four main drivers pushing organizations towards EMPs. It's a confluence of factors. First, and maybe the biggest one. Your attack surface has absolutely exploded. Just think about it. Cloud apps, remote workers everywhere, IoT devices popping up, APIs connecting everything.
Katie: And shadow IT?
James: And tons of shadow IT. Those unmanaged devices, rogue applications that IT doesn't even know about. All this stuff expands your live environment way beyond what old school scheduled scanners can reliably track. Those are blind spots. Huge blind spots. EMPs are designed for this. They continuously discover new assets, even as your environment shifts and changes minute by minute. No more guessing.
Katie: OK, that's huge. What's number two?
James: Second reason. Exploits move faster than ever. We're talking lightning speed. CISA, the U.S. cybersecurity agency, they reported seeing some vulnerabilities exploited in the wild within like 48 hours of being publicly disclosed.
Katie: 48 hours? That's insane.
James: It is. So if you're waiting for your monthly patch Tuesday or relying on slow manual processes to fix things, well, you're leaving a massive window open for attackers.
Katie: Too much time.
James: Way too much time. EMPs directly tackle this by shrinking that time to fix. They automate remediation based on actual business risk, acting much faster.
Katie: Got it. Faster exploits need faster fixes. Makes sense. What's third?
James: Third, CTEM continuous threat exposure management is rapidly becoming the standard. This framework, popularized by Gartner, lays out a cycle. Scope, discover, prioritize, validate, and mobilize.
Katie: We mentioned CTEM earlier.
James: Right. And the key insight here is that an EMP is basically the engine that makes CTEM actually happen in practice.
Katie: Oh, so.
James: Well, it directly supports most of those stages. Discovery, continuous asset and vulnerability finding, prioritization, Using threat intel ceases known exploited vulnerabilities list, asset context, all that smart stuff, mobilization. That's the automated remediation.
Katie: So it operationalizes the CTEM concept.
James: Exactly. It helps you move from just seeing the risks, which CTEM emphasizes, to actually doing something about them consistently and confidently.
Katie: OK. And the final reason.
James: And fourth, maybe the one hitting closest to home for CSOs. Security is now undeniably a business level issue.
Katie: Right. The board wants answers.
James: Precisely. COSOs can't just report, we scanned X systems. They need to communicate risk reduction. The board is asking sharp questions. What's our real exposure right now? What are we actively doing about it?
Katie: And an EMP helps answer that.
James: Directly. They offer executive-ready dashboards. You can track metrics like mean time to remediate MTTR. You can show adherence to internal SLAs. You track your compliance posture. It translates the technical details into business impact and risk language.
Katie: OK, so attack surface explosion, faster exploits, the push for CTEM and business accountability. Those are powerful drivers.
James: Absolutely. They collectively make the old ways insufficient.
Katie: So we've covered the what's the definition and the why, the driving forces. Now let's get into the how. How does an EMP actually deliver this continuous protection? You mentioned a loop. What does that look like in practice?
James: Yeah, the continuous loop is really the operational heart of an EMP. It's designed to replace those stop start often manual processes that just can't keep up anymore.
Katie: Okay, walk us through it.
James: It really boils down to four key steps running constantly. Step one, discover all assets and vulnerabilities.
Katie: Back to that visibility point.
James: Exactly. The platform has to automatically find everything. Servers, laptops, cloud instances, software versions, configurations, across your whole environment, whether it's in the office, remote, hybrid, doesn't matter. Comprehensive, real-time visibility is the foundation.
Katie: Got it. Step one, know what you have. What's next?
James: Step two, analyze and prioritize based on risk. And this is where it gets much smarter than older tools because way beyond just that basic CVSS score. It uses data on actual exploitability. Is this thing really being targeted in the wild? It considers the asset sensitivity. Is this a critical database or just a test machine? It pulls in current threat intelligence. It looks at network exposure. All this gets crunched to calculate the true business relevant risk.
Katie: So understanding what attackers are actually doing and what matters most to us.
James: Precisely. It cuts through the noise to find the real danger signals.
Katie: Okay, discovered, prioritized, then comes the action.
James: Yes. Step three, remediate automatically. This is where the platform really earns its keep, turning that insight directly into protection.
Katie: How does it do that?
James: It can do things like apply patches directly. It can execute custom scripts, maybe to harden a system's configuration. It can isolate a risky device from the network or even apply virtual patches, essentially blocking an exploit attempt before a vendor fix is even ready.
Katie: Wow. Okay. And automated.
James: Often, yes, through workflows triggered by those risk thresholds you set. High risk on a critical server. Boom, action happens.
Katie: That speeds things up dramatically. And the last step.
James: Step four, validate and report. You need to close the loop. Did the fix actually work? Is the vulnerability gone?
Katie: Verification.
James: Right. The EMP confirms the fix, logs all the changes, which is vital for compliance and audits, and provides live up-to-date dashboards showing the current exposure picture for security teams, IT teams, even leadership.
Katie: So discover, analyze, and prioritize, remediate, validate, and report. continuously.
James: That's the loop. And for you, the listener, the big takeaway is this model slashes that alert fatigue. Your teams aren't drowning anymore. And critically, it massively speeds up the time to resolution. It gives you a clear, often automated path from seeing a problem to actually fixing it. Insight to action.
Katie: That continuous cycle makes a lot of sense. But given how broad this is, discovery, prioritization, remediation, what stands out to you about who should actually own exposure management in a company, it really feels like it cuts across traditional IT and security silos.
James: That's a fantastic observation. And honestly, it's a place where implementations can stumble if it's not clear. Without clear accountability, the whole remediation part can really fall flat.
Katie: So what's the best practice?
James: The consensus points towards shared ownership, but with central visibility. It needs coordination.
Katie: Okay, how does that break down typically?
James: Well, generally, the security team owns the discovery piece, the risk analysis, the prioritization. They also usually define the remediation policies, what should happen under what circumstances, and they provide overall oversight.
Katie: Makes sense. They set the strategy.
James: Right. Then your IT operations or DevOps teams, they're often the ones who actually execute the remediation actions, or at least review and approve the automated ones the platform suggests. They're hands on with the systems. OK. And then leadership CISOs, maybe even the CIO or risk committees, they monitor the high level picture. They're looking at those exposure KPIs, the remediation trends, overall risk reduction, usually through those dashboards we talked about.
Katie: So the EMP acts as a bridge between these groups.
James: Exactly. A good EMP is designed for this. It has integrated workflows, role-based access control so people only see what they need to, and policy governance features. It ensures everyone's working from the same playbook, not operating in separate silos. It really fosters that team approach.
Katie: A team sport, as you said. Okay, so for someone listening who's thinking, all right, this sounds powerful, maybe we need this, or they're starting to evaluate different solutions, what are the absolute must have capabilities, like the top five things to look for in a strong EMP? What really moves the needle?
James: That's a great question for anyone considering this. If you're really focused on driving down risk and making security operations more efficient, I'd highlight these five capabilities as absolutely critical. Okay. Number one. First, comprehensive cross-platform patching. This is foundational. The EMP has to be able to patch not just Windows, but also Linux, back OS, and a wide range of common third-party applications, think browsers, productivity tools, et cetera.
Katie: Across different environments, too.
James: Yes, across desktops, servers, and cloud workloads. If it can't cover your whole estate, you're going to have significant gaps in manual workarounds, which defeats the purpose. Full coverage is key.
Katie: Makes sense. What's second?
James: Second, policy-based auto-remediation. This capability is a massive efficiency booster. It lets the security team pre-define rules.
Katie: Like the example you get earlier.
James: Exactly. Like if a CVE has a known exploit and it affects a high value server, then automatically apply the vendor patch and notify the IT server team.
Katie: So it takes action based on rules.
James: Right. It ensures swift, decisive action on the riskiest things without needing a human to manually click approve every single time. That manual step is often a huge bottleneck.
Katie: I can see that. Number three.
James: Third, real-time actionable dashboards and reporting. This isn't just about pretty charts. You need dashboards that clearly track your current open exposures, how quickly you're fixing things, remediation velocity, whether you're meeting your internal SLAs and your exposure broken down by important categories like business unit, asset type, or location.
Katie: Why is that so critical?
James: It's vital for audits, absolutely essential for reporting progress and posture to leadership, and it's how you measure success and drive continuous improvement in your program. You can't manage what you can't measure effectively.
Katie: True. Okay, number four.
James: Fourth, AI-driven or advanced prioritization. We touched on this, but it bears repeating. The platform needs to go beyond basic CVSS. It should leverage real-time exploit intelligence, understand the specific context and criticality of your assets, maybe even use behavioral analytics to score risk much more accurately.
Katie: So it focuses you on what's actually likely to hurt you.
James: Precisely. It helps you allocate your limited resources to the threats that pose the greatest danger to your specific organization right now.
Katie: And the fifth capability.
James: And fifth, crucially, strong integration with your existing security and IT stack. An EMP can't live in a vacuum. It must integrate smoothly with the tools you already use.
Katie: Like what?
James: Like your SIEM system, maybe Splunk, maybe Sentinel, your SOAR platform for broader automation, Cortex-XOSR, for example, your ITSM system for ticketing and change management service now, JIRA, also your EDR, your CMDB for asset info, maybe even identity systems.
Katie: So it becomes part of the ecosystem.
James: Exactly. It needs to fit naturally into your overall security operations workflow, sharing data back and forth, not just becoming another isolated tool that adds complexity. Seamless integration is key for operational success.
Katie: Cross-platform patching, auto remediation policies, real-time reporting, AI prioritization, and snack integration. That's a solid checklist.
James: Those are definitely table stakes for an effective EMP.
Katie: Now, to make this even more concrete, let's talk about some real-world applications. Can you share a few examples of how organizations are actually using EMPs to get tangible security wins right now?
James: Yeah, absolutely. Seeing it in action really brings it home. Let's look at a few common use cases. OK, use case one, proactively reducing ransomware exposure. This is top of mind for everyone. Imagine a major ransomware advisory comes out listing, say, three specific CVEs that attackers are actively exploiting.
Katie: A typical fire drill scenario.
James: Right. But with a robust EMP, one source mentioned, Vicarious' VRX as an example. Doing this, the platform can automatically swing into action. It instantly identifies all the systems vulnerable to those specific CVEs across the entire network.
Katie: Okay, fast identification.
James: Then for systems where vendor patches are available, it can automatically deploy them. For others, maybe zero days or older systems without patches, it might apply other protections like memory level exploit prevention.
Katie: Virtual patching or similar technique.
James: Exactly. And the key is this can happen within hours of the advisory, not days or weeks. It drastically shrinks that window the ransomware actors have to get in. Proactive automated defense.
Katie: That's impactful. What's another example?
James: Use case two, enforcing system hardening policies. Think about a company in a regulated industry like finance. They need to maintain really tight security configurations on their endpoints.
Katie: Compliance requirements.
James: For sure. So they could use the scripting capabilities often found in EMPs to automate specific hardening tasks across, say, all their Windows machines.
Katie: Like what kind of tasks?
James: Things like automatically disabling old insecure protocols like SMBV1, blocking potentially dangerous office macros that aren't digitally signed, enforcing strong password complexity rules. The EMP ensures these settings are applied consistently everywhere at scale without needing an engineer to touch every single machine.
Katie: Automation for consistency and compliance. Got it. One more.
James: Use case three. Streamlining continuous compliance maintenance. Let's take a health care organization. They live under regulations like IP. Compliance isn't a one-time check. It's ongoing.
Katie: And constant pressure.
James: Right. So an EMP's dashboard has become incredibly valuable. It can continuously monitor and track the remediation progress specifically for all systems handling patient data, PHI, ensuring vulnerabilities on those critical assets are being addressed within policy timelines.
Katie: Real-time visibility for compliance.
James: Exactly. And then when audit time comes, they can often export the necessary audit logs and reports directly from the EMP platform, making that whole evidence gathering process much faster and less painful.
Katie: Ransomware defense, policy enforcement, compliance upkeep. Those are definitely compelling applications.
James: They show how EMPs move beyond just finding flaws to actively improving security posture in very practical ways.
Katie: So bringing this all together, what does this evolution towards exposure management really mean for the future of cybersecurity? And maybe more importantly, for you, our listener, who's out there dealing with these threats day in and day out.
James: Well, I think the core takeaway, the bottom line, is becoming crystal clear. just doing vulnerability scanning the old way. It's simply not enough anymore. It can't keep pace.
Katie: The landscape changed too much.
James: It absolutely has. Cyber risks evolve minute by minute. Security teams are overwhelmed. They need more than just lists of potential problems. They need efficient, reliable action. They need scale.
Katie: And the EMP provides that action.
James: That's exactly what an exposure management platform is designed to deliver. That continuous insight into your real risk, the intelligent, real-time prioritization telling you what matters most now, the automated remediation to actually fix things quickly, and crucially, the measurable results to prove effectiveness in guide strategy.
Katie: So whether you're trying to align with the framework like CTEM.
James: Or needing to report your security posture clearly to your board.
Katie: Or maybe just desperately trying to shrink that massive, never-ending patch backlog.
James: The right EMP can transform all that security data you're collecting into actual, tangible protection for your organization.
Katie: So the future belongs to platforms that act.
James: I firmly believe so. The future of cybersecurity belongs to platforms that enable action. Exposure management isn't just a good idea or a future goal anymore. For resilience in today's world, it's becoming an absolute requirement.
Katie: A requirement. That's a strong statement, but based on everything we've discussed, it makes sense. We've really covered a lot today, unpacking the critical shift from just finding vulnerabilities to actively managing and fixing exposure risk using these exposure management platforms.
James: We saw how EMPs deliver that continuous insight, the smart real-time prioritization and the automated action that's just essential now, given how fast the threats move.
Katie: Absolutely. Now, building on that idea you just shared that the future of cybersecurity belongs to platforms that act, maybe here's a final thought for you, our listener, to chew on. How much more secure could your organization genuinely be if you made that consistent leap? Moving beyond just knowing about vulnerabilities to consistently acting on the riskiest ones with automated, prioritized fixes.
James: It's a powerful question.
Katie: What immediate insights could you unlock and what critical actions could you take, maybe even starting today, if you knew with confidence exactly where your most valuable assets were truly exposed and you actually had the tools ready to fix those exposures at machine speed?
James: That's the potential here.
Katie: That really is the power we've been talking about, the power of turning overwhelming data into tangible measurable protection.
James: Well said. It's about making security proactive, not just reactive.