In a year marked by escalating digital threats, vulnerability exploitation has emerged as a dominant vector in data breaches. According to the 2025 Verizon Data Breach Investigations Report, exploitation is now implicated in 20% of all breaches, closing in on credential abuse as the leading method of initial access from just under 15% the previous year.
The report highlights a 34% year-over-year rise, driven largely by the growing automation and scale of opportunistic attacks targeting known software flaws. Edge infrastructure has become a focal point of these intrusions. Devices serving as gateways between internal networks and the internet, such as Citrix NetScaler and Cisco ASA, were linked to nearly a quarter of exploitation-based breaches in 2025. That figure represents an eightfold increase over the previous year, underscoring how attackers are prioritizing targets with high privilege access and wide attack surfaces.

The three most common attack patterns
Despite growing awareness and available patches, organizations continue to struggle with timely remediation. The median time to patch a known vulnerability remained at 32 days; ample time for adversaries to scan for and weaponize unaddressed flaws, given the hyper-accelerating effect AI has had on shortening exploit development timelines. In many cases, attackers are exploiting vulnerabilities within days of public disclosure, turning any delay into a direct path to compromise. The attack surface may be vast, but the methods used to breach it tend to follow repeating patterns - patterns that defenders can recognize and prioritize against.
Let’s take a closer look at the three of most common attack patterns:
- Remote code execution on edge-facing devices: The first and most dangerous of these is remote code execution (RCE) in edge-facing devices. RCE vulnerabilities in Citrix NetScaler and Cisco IOS XE, for example, have enabled attackers to deploy malware, modify configurations, and gain persistent access, sometimes without even requiring authentication. These devices often run legacy firmware or expose overly permissive management interfaces, which means attackers can exploit them with relatively little effort and high reward.
- Authentication and session bypass flaws: A second and frequently overlooked pattern involves authentication and session bypasses. Atlassian Confluence and similar enterprise tools have suffered from flaws that allow attackers to bypass login requirements altogether. These aren't simply isolated bugs, though - they often act as force multipliers. When paired with RCEs or local privilege escalation vulnerabilities, they let attackers persist long after initial access, blending into legitimate traffic and users.
- Persistent exploitation of known CVEs: The third pattern is perhaps the most frustrating for defenders: the exploitation of known, patchable CVEs. Time and again, organizations fall victim to vulnerabilities disclosed - even patched - months or years earlier. Configuration drift, legacy systems, and unmanaged assets all contribute to this persistence. The result is a slow-moving but ever-present threat landscape, in which yesterday’s headlines become tomorrow’s breach vector.
This isn’t just an operational bugbear - it's a signal: vulnerability management strategies that rely on triage alone are failing. Without treating configuration management and patch hygiene as continuous, high-priority efforts, even the best alerting tools become reactive at best.

KEV as the north star for prioritization
When everything is urgent, nothing is. This is why the CISA Known Exploited Vulnerabilities (KEV) catalog has become such a critical resource: instead of merely flagging every CVE with a “high” CVSS score, KEV focuses only on vulnerabilities confirmed to be actively exploited in the wild. It transforms triage from a theoretical exercise into a field report, since this is what attackers are actually using. Security teams that align their workflows with KEV are better positioned to act decisively. Instead of getting lost in a sea of “critical” ratings, they can focus limited resources on provable threats. In fact, KEV often highlights vulnerabilities that might not look severe on paper but are weaponized due to their ubiquity or exposure vector.
More importantly, KEV changes the structure of remediation programs. It gives teams a clear basis for patch prioritization, simplifies executive reporting, and clarifies remediation SLAs. By subscribing to KEV updates and embedding them into existing vulnerability scanners or asset management platforms, organizations can automatically flag affected systems and reduce manual overhead. What KEV offers is not a replacement for CVSS, but a reality check - it filters and, to a degree, curates the noise and aligns remediation efforts with real-world threat activity, ensuring teams stay ahead of attackers rather than merely reacting to them.
Accelerating remediation with vRx
vRx by Vicarius translates KEV insight into operational speed. Our platform continuously ingests the KEV catalog and maps it directly onto your live asset inventory, thereby eliminating the need for manual correlation or custom scripting by highlighting in real time which machines are exposed to actively exploited vulnerabilities and which are safe.
What sets vRx apart is its remediation engine. Unlike traditional patch management systems, vRx uses agentless, ringed rollout strategies with built-in rollback support. This means patches can be deployed in tightly scoped waves, starting with low-risk devices and escalating as confidence grows. If something breaks, you can roll it back with a single click.
Often the missing link between policy and practice, this kind of operational insight into what was patched, what wasn’t, and why, is. With vRx, that gap disappears. It’s not just about patching either - our stack delivers a complete trail of remediation activity, from dashboards and live SLA tracking to downloadable audit reports. Whether it’s internal oversight or external compliance, teams can demonstrate exactly when, where, and how they responded to known threats.

Operationalizing SLAs and playbooks for KEV-first remediation
Setting patching timelines isn’t simply about establishing benchmarks - it’s about reinforcing trustworthiness and credibility. A well-defined SLA signals not just intent but the organization’s actual ability to respond at speed, under pressure, and with accountability. In a KEV-driven model, the timelines must reflect real attacker behavior and actual system exposure.
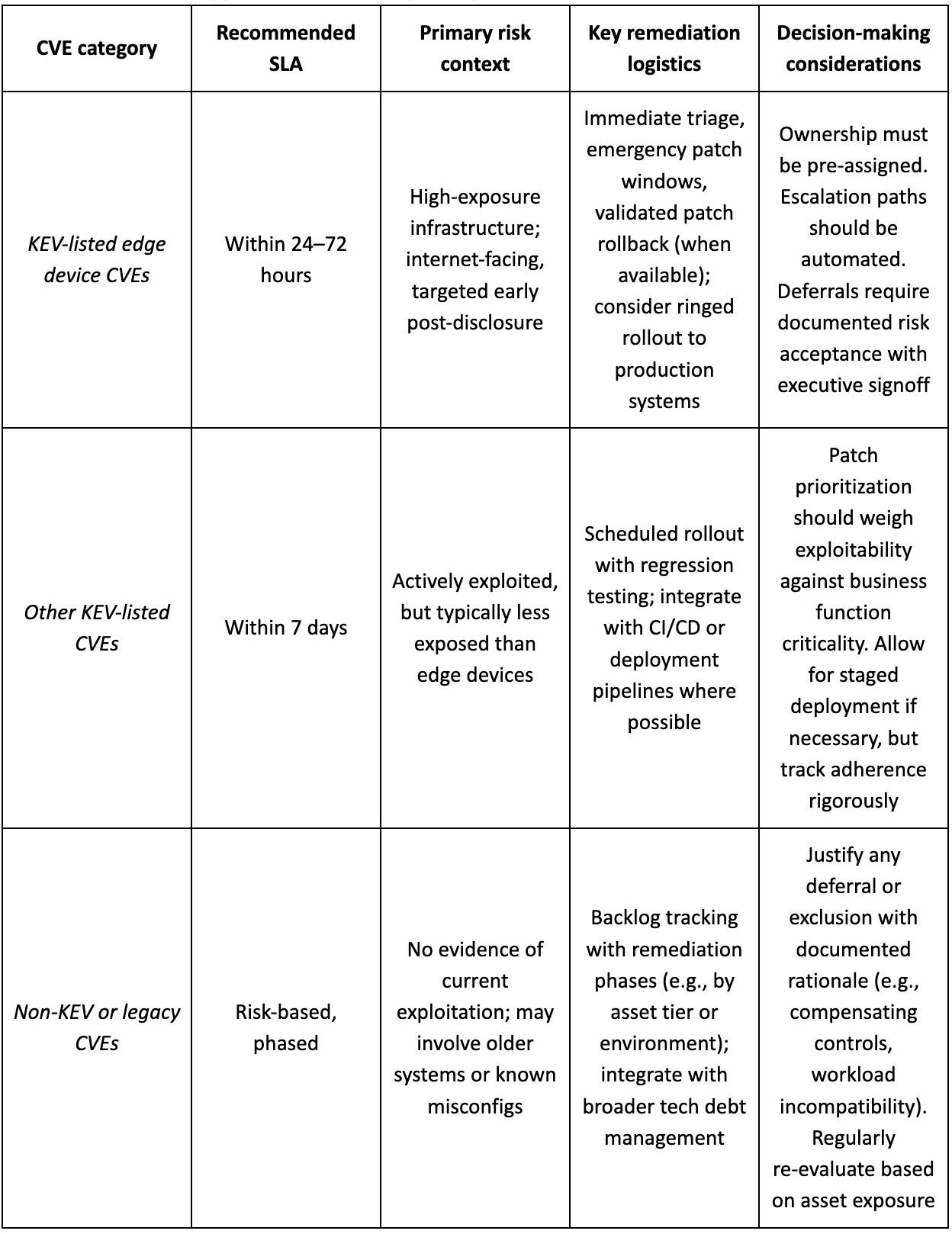
To help formalize this approach, the following table provides a tiered SLA reference:
Timelines alone are insufficient, though. For KEV-first remediation to be successful, execution must be embedded in day-to-day operational workflows. That means transforming policy into practiced muscle memory through the following playbook components:
- Integrated KEV awareness: Ensure scanners, asset inventories, and ITSM platforms ingest KEV data and tag affected assets automatically.
- Role clarity and escalation: Designate owners for remediation, risk acceptance, and exception approvals. Escalate any missed SLAs automatically.
- Patch validation protocols: Define test, staging, and deployment processes (especially for edge devices) to prevent service disruption.
- Tabletop exercises: Run simulated breach scenarios based on real KEV entries to evaluate response timelines, coordination, and rollback readiness.
The common thread here is operational realism. A KEV-first strategy works only when SLAs are sustainably achievable, ownership is unambiguous, and execution is continuously tested. Otherwise, it’s just policy on paper. Done right, this approach not only reduces breach likelihood but creates something security leaders can stand behind when scrutiny comes: a security framework that is demonstrably more secure - and which brings the receipts come crunch time.
Learning practical KEV-first remediation strategies
Security programs that rely solely on CVSS-based triage are increasingly out of step with today’s threat landscape. Attackers are moving faster, and their priorities are informed by exploitability, not severity scores. KEV helps teams keep pace by focusing effort where it matters most. Organizations that operationalize KEV into their workflows benefit from faster remediation cycles, tighter audit trails, and a demonstrably lower breach surface. The business case is clear: fewer incidents, shorter incident response timelines, and stronger compliance posture.
To assist your team in getting there, Vicarius offers a KEV-first remediation workshop. This session assesses your current exposure, maps your remediation flows to the KEV model, and shows you how to fast-track patching with vRx. The difference isn’t just in how you patch - it’s in how confidently you can prove it. Book today to discover how we can help you love the patch again!