
On 10 September 2025, the Cybersecurity and Infrastructure Security Agency (CISA) published its roadmap titled “CVE Quality for a Cyber Secure Future”, signaling the transition of the Common Vulnerabilities and Exposures Program (CVE) from a phase of expansive growth to one of deliberate guardianship. This marks a significant pivot: vulnerability intelligence is no longer simply a tool for technical teams; it is now a regulated component of enterprise risk programs, subject to the same oversight and audit scrutiny as other high-stakes regulatory inputs. Boards and compliance officers must recognize that this regulatory framing elevates responsibilities not only for cybersecurity operations, but for governance frameworks, reporting structures, and supplier transparency.
In practical terms, governance expectations are changing: organizations must prove that they act on credible regulatory signals, not just receive them. Leadership must ensure mechanisms exist so that once a vulnerability is flagged, the sequence of interpretation, assignment of ownership, mitigation, and validation is traceable, time-bound, and defensible under review. For compliance officers, this means clarifying which teams are accountable for each link in the chain, what results they must deliver, and when they must deliver them. Effective oversight now depends on removing ambiguity about who must prove what, by when, and to whom.
This article is Part 4 of our series on the CVE Program Vision and Future Outcomes. With Part 1 defining the Quality Era, Part 2 highlighting automation-ready infrastructure, and Part 3 establishing transparency and shared accountability across the software supply chain, this installment turns the focus to governance. We examine how boards, compliance leaders, and executive risk owners can operationalize these modernization efforts into continuous assurance, ensuring that when regulators raise the alarm, organizations are ready to demonstrate timely action, verifiable closure, and defensible cyber due diligence.

The quality era for vulnerability intelligence: Decisions, not data
Regulatory investment in higher-quality vulnerability data means the bottleneck is no longer collection but decision-making. Machine-readable records allow risk classification and response planning to happen within the decision windows expected of senior leadership, not at the pace of manual research. As the quality of signals improves, the burden shifts to boards and compliance officers to ensure their organizations are structured to act on those signals at speed.
To support governance without drowning leaders in operational details, a short set of service objectives should be defined and reviewed consistently. Governance metrics can include:
- Time to classify risk: The interval from regulatory signal to documented business impact and responsible owner.
- Time to mitigation commitment: The interval to an approved and scheduled action path that is proportionate to severity.
- Time to verifiable closure: The interval to objective proof that the exposure is removed or controlled, not merely acknowledged.
A structured triage model reinforces duty of care. When authoritative signals escalate a vulnerability to high-urgency status, boards must be able to confirm that default actions occur without delay, exceptions are controlled, and defensibility is preserved during scrutiny following an incident or regulatory inquiry.
Transparency as assurance in software supply chain accountability
Transparency is replacing trust as the basis for supply chain assurance. Software bills of materials and exploitability status reports have become the expected evidence set for validating vendor claims. They allow compliance leaders to confirm which components are present, whether relevant vulnerabilities are exploitable, and how suppliers are managing downstream impacts. This reduces blind spots and strengthens contractual enforcement of software security obligations.
The policy urgency is clear. If a vulnerability becomes actively exploited or is elevated by regulators, leadership must ensure that all affected systems inside their organization can be identified within hours. This traceability underpins credible reporting to investors, customers, and oversight bodies and supports faster containment of emerging exposures.
Boards have a role in defining how accountability is shared across the chain. Suppliers must guarantee timely intelligence. MSPs must act as stewards of customer environments with clearly defined escalation parameters. Internal operators must maintain authoritative inventories and execution capabilities. Procurement reinforces these expectations by requiring disclosure deliverables, performance-linked renewals, and prompt vendor participation when shared risks emerge.
Auditable remediation turns response into report-ready assurance
A remediation effort is only defensible when it creates a complete, chronologically coherent narrative from signal to closure. Boards and compliance leaders must ensure that every critical vulnerability progresses through a standardized chain of custody that documents who decided what, when, and why. As this evidence is often scrutinized long after actions are taken, the goal is to ensure it is automatically generated by the workflow itself, not assembled under pressure during an investigation or audit.
Core governance indicators for remediation assurance
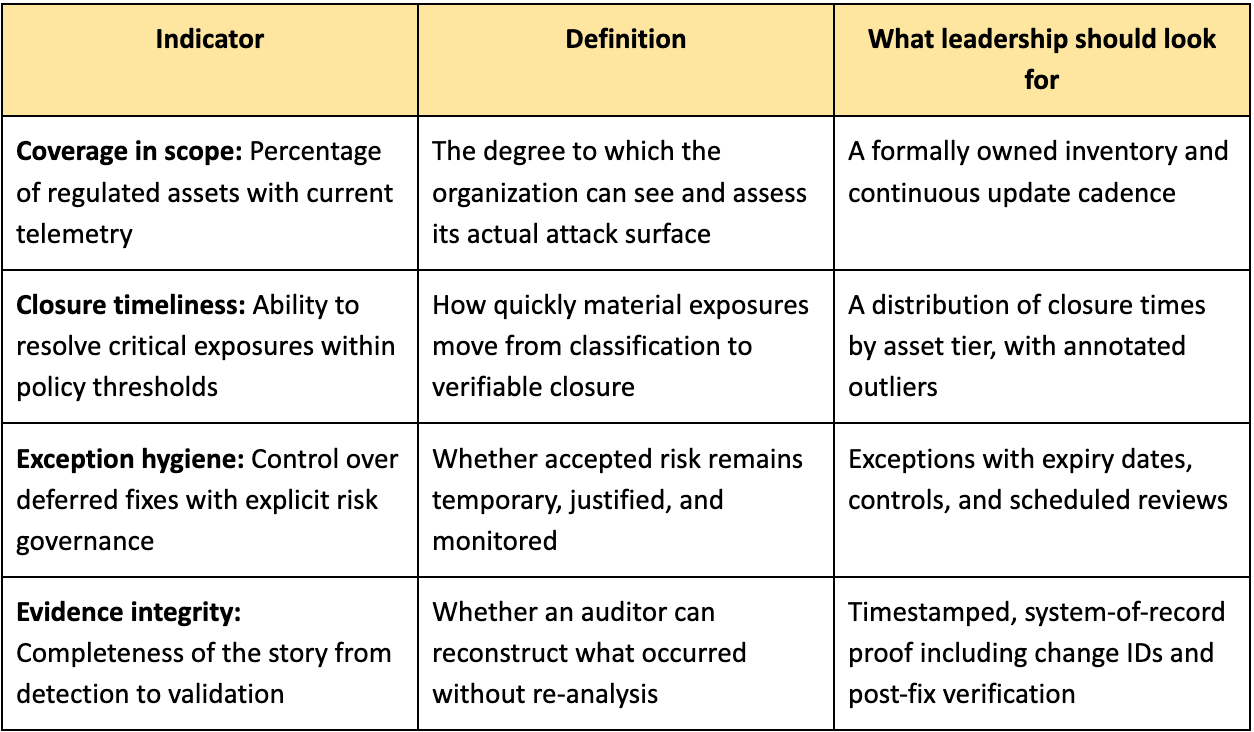
Boards do not need to micromanage remediation itself; they must insist that every action produces durable evidence capable of withstanding external scrutiny.
Aligning platform patterns with regulatory direction
Boards do not need to arbitrate tooling preferences, but they do need to insist on operational designs that produce traceability and evidence as a native feature of day-to-day work. The most strategic investments focus on automation, normalization, and a single system of record capable of showing how a vulnerability signal became a closure decision and, ultimately, a validated reduction in risk. When these fundamentals are in place, technology choice becomes a matter of efficiency rather than compliance survival.
Leadership can help shape a future-proof architecture by insisting on clear seams between the parts that sense risk, the parts that decide what to do, and the parts that implement change. This separation allows regulatory updates, new reporting expectations, or supplier transparency rules to be absorbed as configuration refinements instead of multi-year transformation programs. It also creates a durable governance benefit: the fewer manual gaps between phases of the lifecycle, the fewer opportunities for misinterpretation, delay, or silent failure.
Priorities for lowering exposure time without raising friction:
- Early detection in development: Policies that surface vulnerable dependencies before they reach production environments.
- Safe defaults in deployment: Runtime conditions that automatically block or contain risky configurations without waiting for human approval.
- Embedded evidence capture: Execution paths that automatically attach change proofs and verification results, reducing burden while increasing accuracy.
The unifying principle is operational clarity. When signals, decisions, and actions are tightly coupled and consistently logged, governance becomes insight instead of trust, and regulatory alignment becomes the path of least resistance.

Routine readiness, measurable compliance
Audit-readiness is no longer a milestone tied to an examination window. It is a continuous state of provable control. For executives, this means visibility into which exposures remain unresolved, whether their associated actions are owned and time-bound, and where suppliers must step in to address upstream weaknesses. Sustainable readiness depends on a recurring governance rhythm that reinforces accountability: regular posture reporting to the board, verification that remediations deliver actual risk reduction, and supplier transparency checks that keep dependencies from becoming blind spots.
For organizations constrained by capacity or tooling complexity, simplification becomes essential. Exposure-centric platforms such as vRx by Vicarius align vulnerability signals, decision routing, fix execution, and evidence capture within a single operating loop.
Book a demo today to discover how that alignment reduces staff effort, compresses the delay between detection and mitigation, and ensures leadership receives accurate, defensible status without translation overhead. The end state is not faster patching alone, but a posture that feels inspection-ready every day – It could be your reality.





.png)






